TryHackMe: Warzone 2 Write-up
Introduction
Challenge Link: Warzone 2
An alert triggered: Misc activity, A Network Trojan Was Detected, and Potential Corporate Privacy Violation. Inspect the PCAP and retrieve the artifacts to confirm this alert is a true positive.
Tools:
- Brim
- Wireshark
Investigation Steps
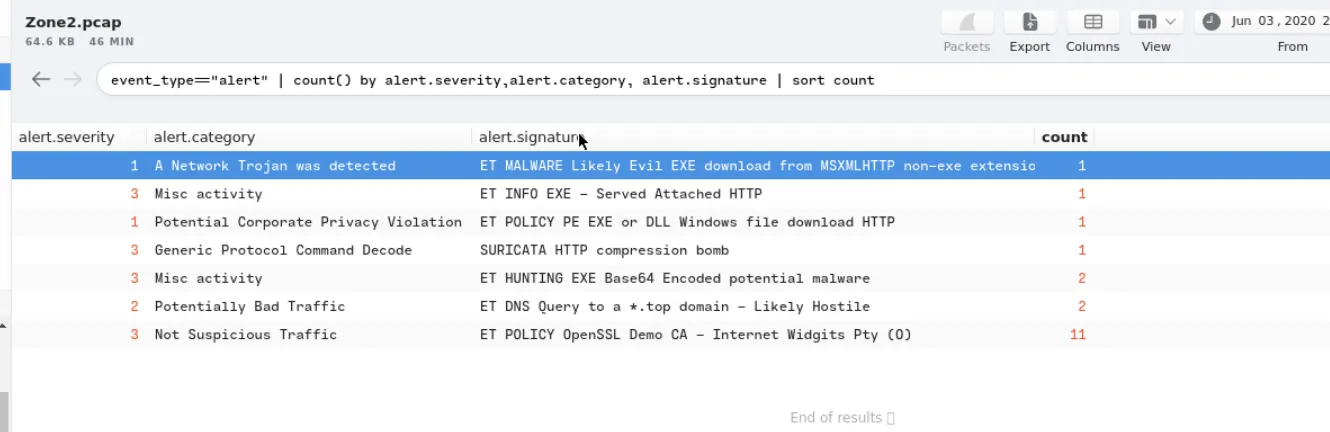
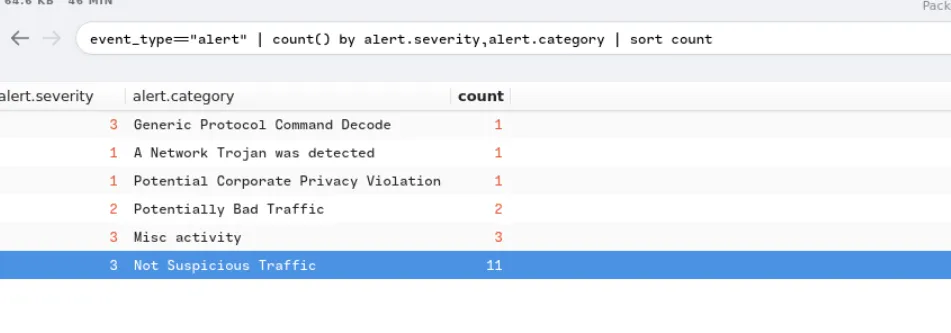
First, check the generated alerts using Brim
1
event_type=="alert" | count() by alert.severity,alert.category, alert.signature | sort count
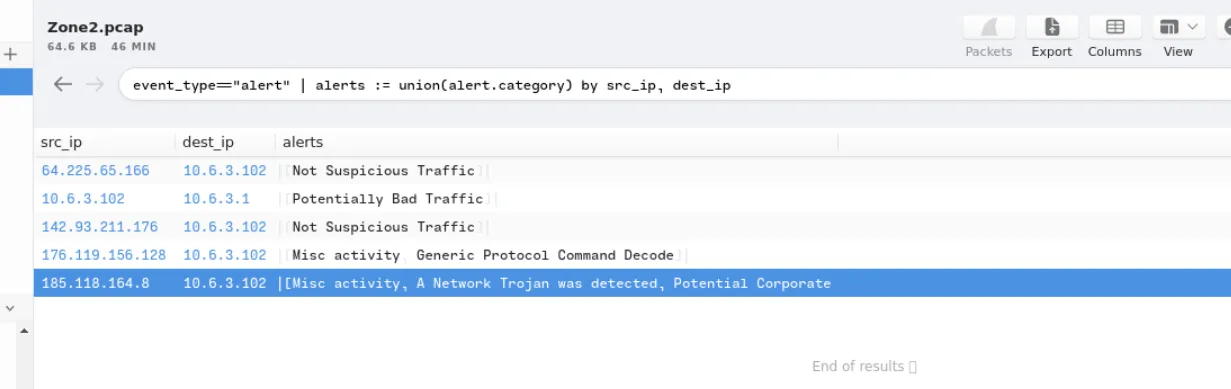
Check the associated IP addresses
1
event_type=="alert" | alerts := union(alert.category) by src_ip, dest_ip
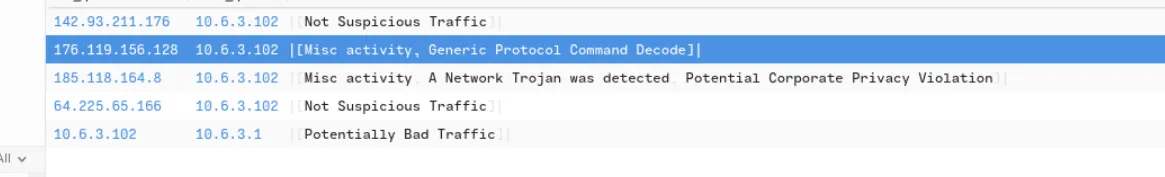
This IP “185[.]118[.]164[.]8” triggered A Network Trojan was Detected and Potential Corporate Privacy Violation alerts.
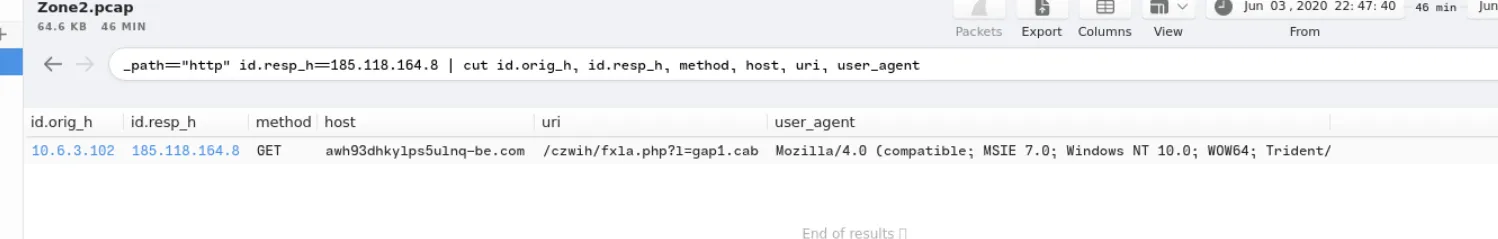
Check the HTTP traffic associated with the suspicious IP
1
_path=="http" id.resp_h==185.118.164.8 | cut id.orig_h, id.resp_h, method, host, uri, user_agent
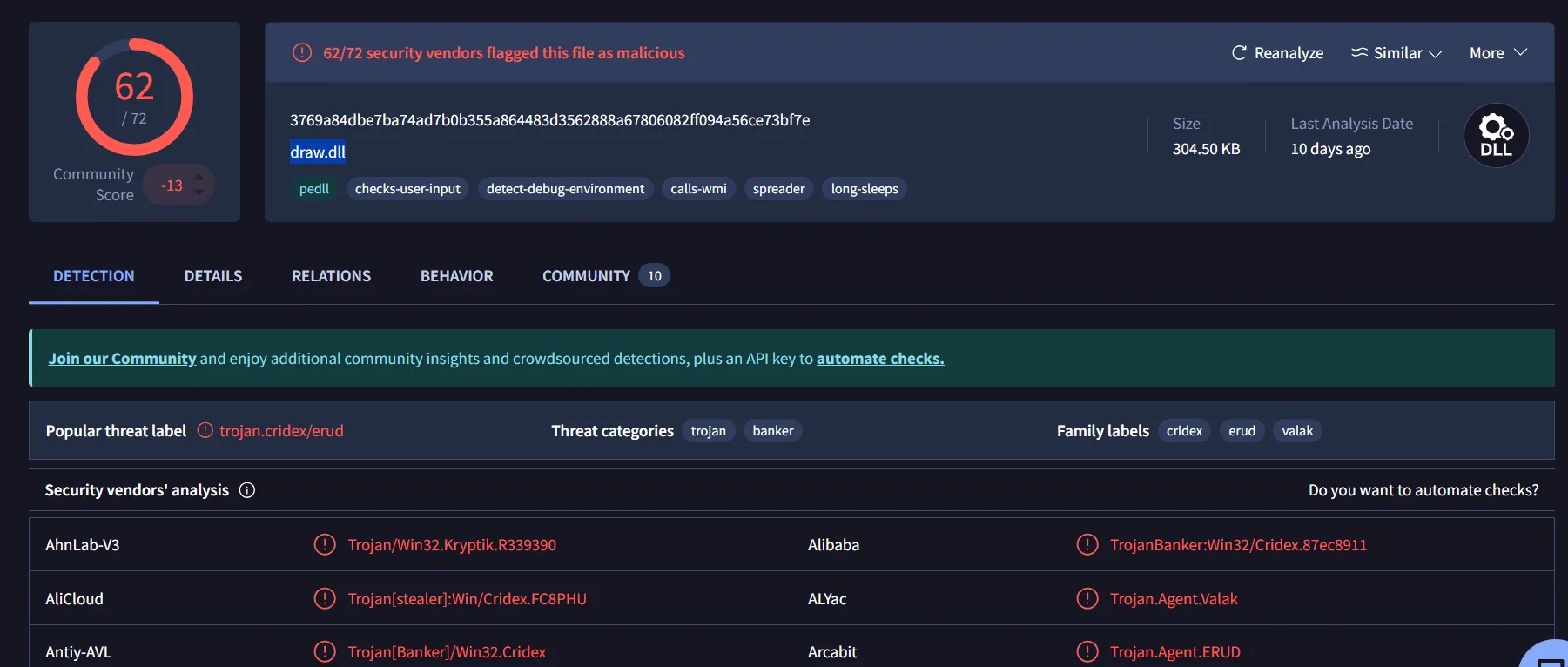
The domain host associated with the IP address was flagged as malicious by VirusTotal, and the user attempted to download a file from the domain.
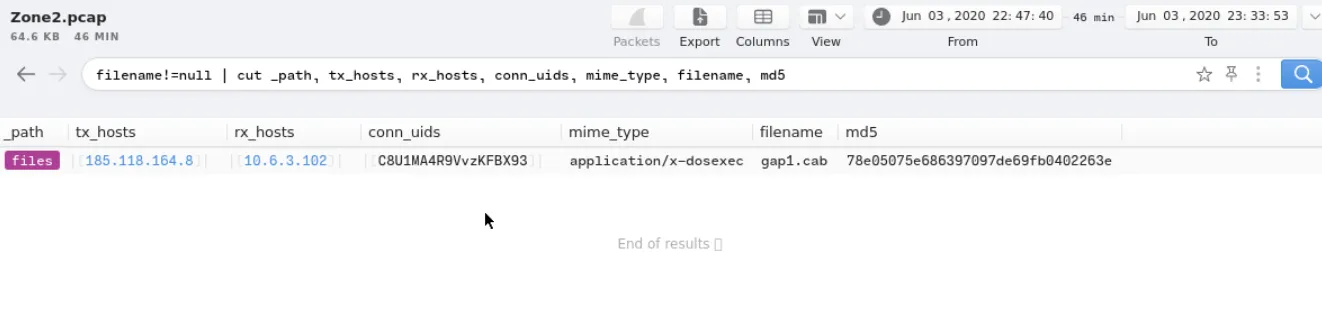
View the file activity and check the file hash in Virustotal.
1
filename!=null | cut _path, tx_hosts, rx_hosts, conn_uids, mime_type, filename, md5
The file hash confirmed that the file is a Trojan malware; thus, the alert ‘A Network Trojan was Detected’ and ‘Potential Corporate Privacy Violation’ is a True Positive.
Check the second generated alert “Generic Protocol Command Decode, Misc activity” from the IP 176[.]119[.]156[.]128.
- Generic Protocol Command Decode: This means the system detected someone using a standard network protocol (like web browsing or email) in an abnormal, non-standard, or suspicious way.
- Misc activity: This is a general catch-all category for any suspicious activity that doesn’t fit a specific known threat.
To confirm if the alert is a True Positive, check the reputation of the source IP in VirusTotal
1
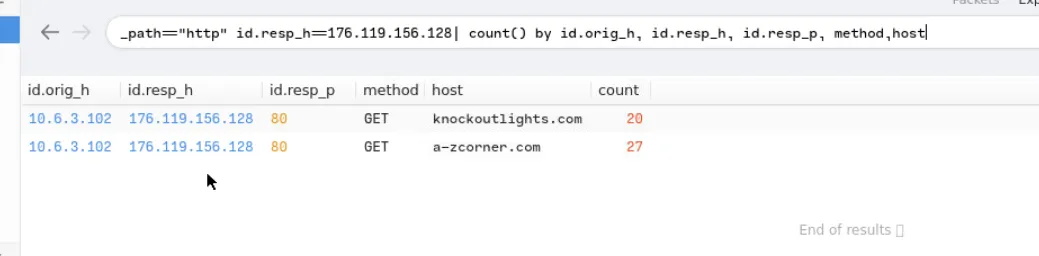
_path=="http" id.resp_h==176.119.156.128| count() by id.orig_h, id.resp_h, id.resp_p, method,host
These two domains were associated with the IP, and they were flagged as malicious.
Thus confirming that the alert is a True Positive
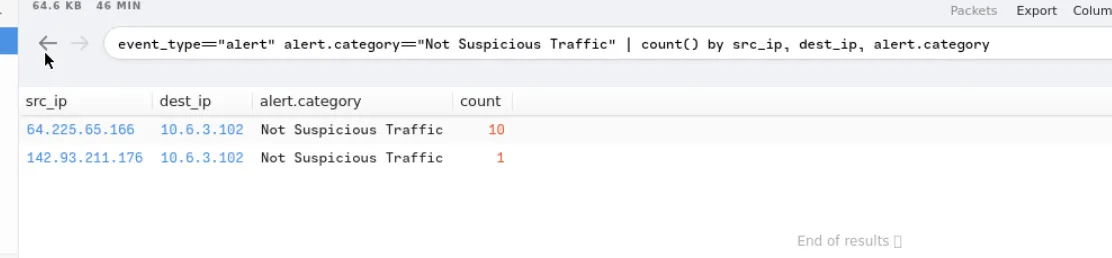
For the last alert, “Not Suspicious Traffic”, we need to confirm whether it’s truly safe or a false negative
Check the associated IPs
1
event_type=="alert" alert.category=="Not Suspicious Traffic" | count() by src_ip, dest_ip, alert.category
1
64[.]225[.]65[.]166,142[.]93[.]211[.]176
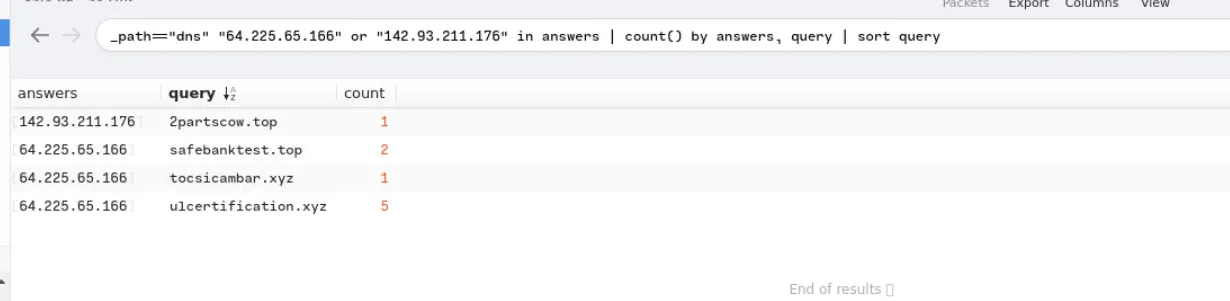
Also, check the associated domains
1
_path=="dns" "64.225.65.166" or "142.93.211.176" in answers | count() by answers, query | sort query
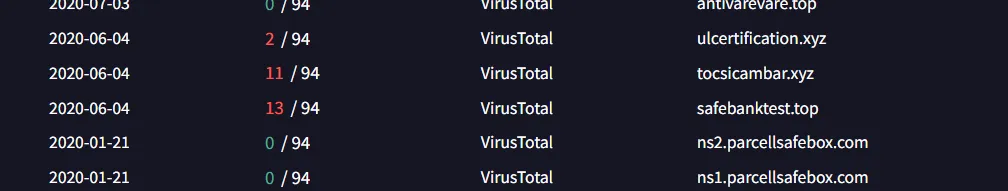
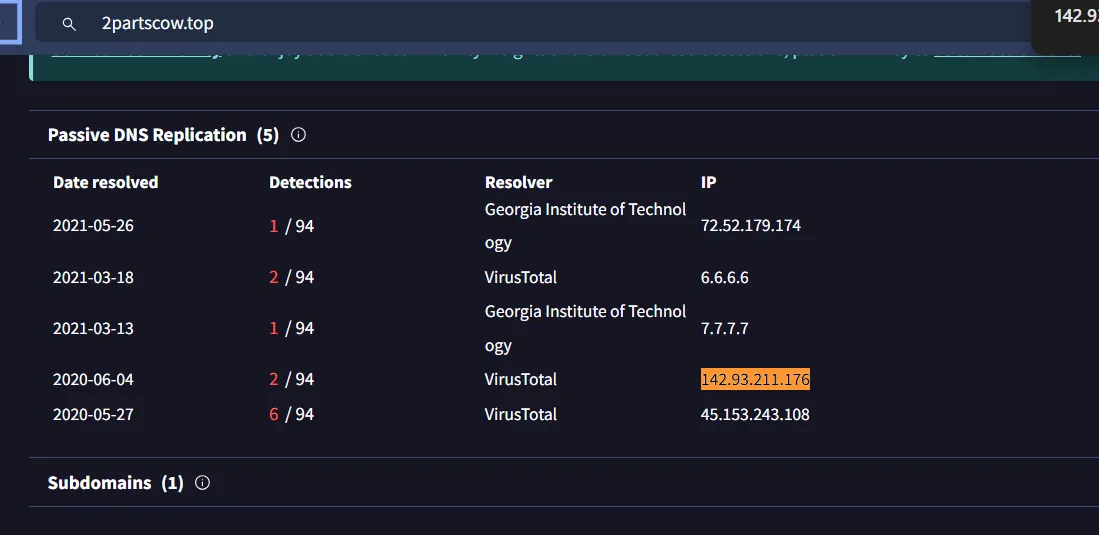
When I searched for the IP address “64.225.65.166” in Virustotal, I found three domains associated with this IP address were flagged as malicious
As for the second IP, upon checking the associated domain in VirusTotal, the IP was flagged as malicious.
Thus, the alert is False Negative, the system incorrectly flagged a malicious traffic as “Not Suspicious.”
Conclusion
Analysis of the PCAP confirms a multi-stage attack with both accurate and missed alerts:
“A Network Trojan Was Detected” & “Potential Corporate Privacy Violation”:
True Positive. A file (
update.axd) was downloaded from a malicious IP (185.118.164.8). The file’s MD5 hash is a known Trojan, confirming malware execution and data exfiltration risk.“Generic Protocol Command Decode” & “Misc activity”:
True Positive. Traffic to IP
176.119.156.128(linked to malicious domains) used protocols in a non-standard, suspicious manner, justifying the alert.“Not Suspicious Traffic”:
False Negative. The system incorrectly cleared traffic to known malicious IPs (
64.225.65.166,142.93.211.176). These endpoints have poor reputation scores and should be treated as threats.