TryHackMe: Warzone 1 Write-up
Introduction
Challenge Link: Warzone1
An alert triggered: Potentially Bad Traffic and Malware Command and Control Activity detected. Inspect the PCAP and retrieve the artifacts to confirm this alert is a true positive.
Tools:
- Brim
- Wireshark
Investigation Steps
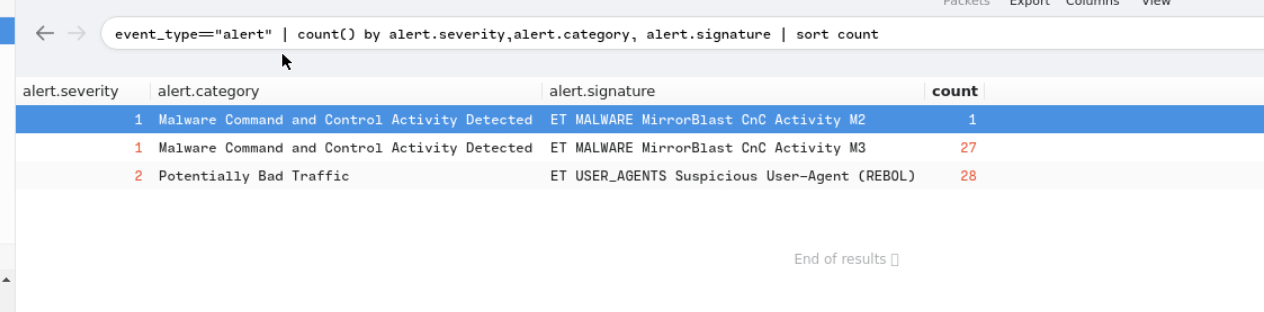
Check the generated alerts using Brim.
1
event_type=="alert" | count() by alert.severity,alert.category, alert.signature | sort count
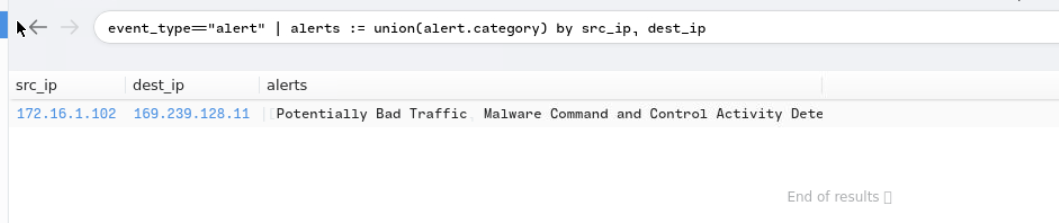
Find the source IP associated with the generated alerts
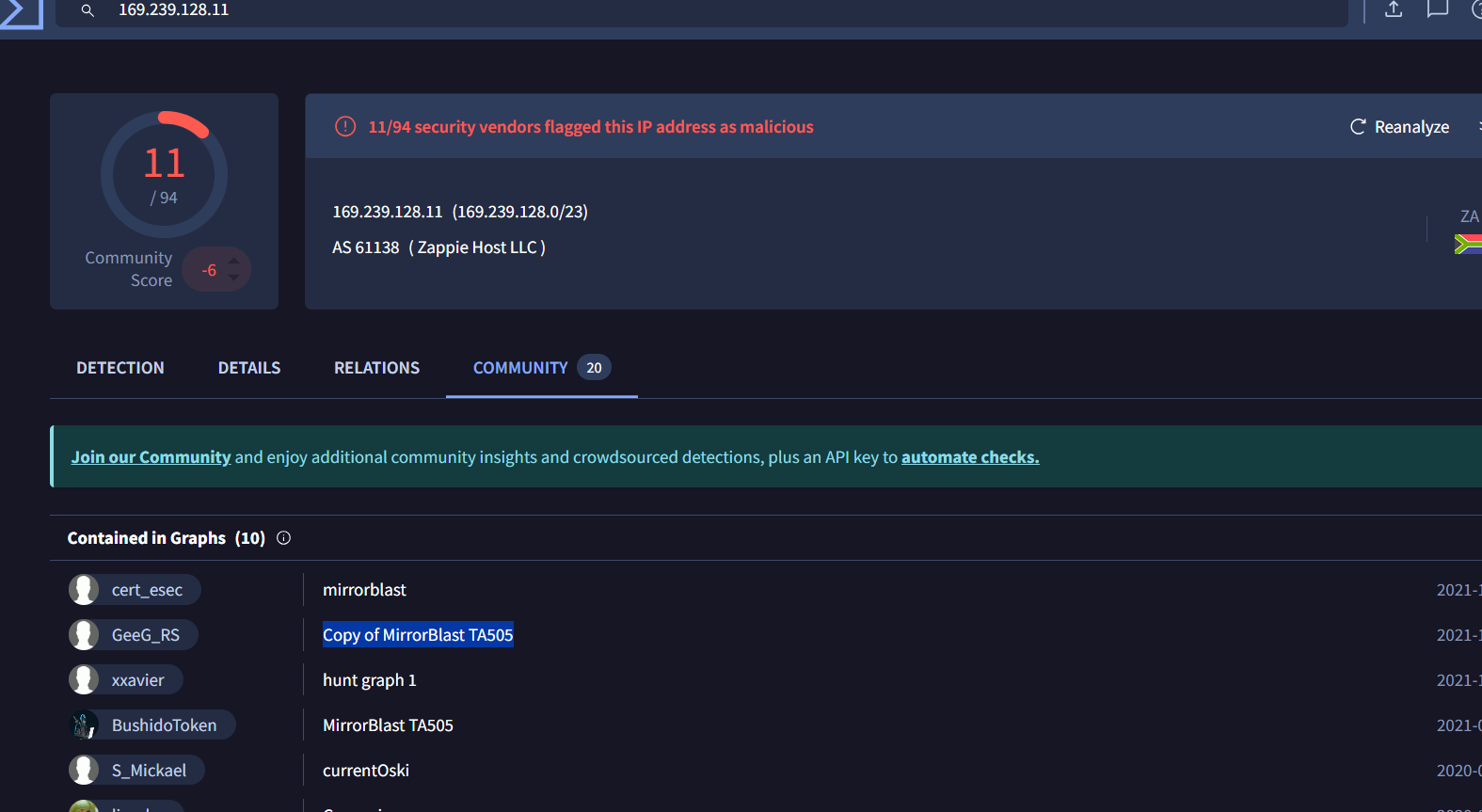
Examine the reputation of the IP in VirusTotal.
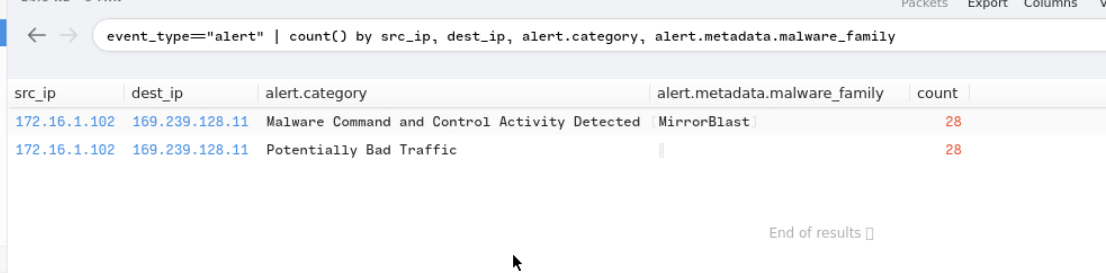
Upon checking the community tab, I found that the IP address is attributed to the threat group TA505. Check the downloaded malware family
1
event_type=="alert" | count() by src_ip, dest_ip, alert.category, alert.metadata.malware_family
Now inspect the web traffic for the flagged IP address
1
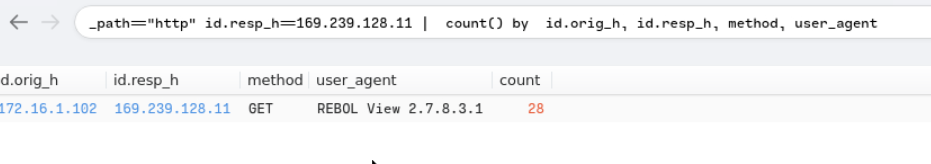
_path=="http" id.resp_h==169.239.128.11 | count() by id.orig_h, id.resp_h, method, user_agent
REBOL is a “multi-paradigm dynamic programming language” that was designed to be used for network communications and distributed computing. According to this article, REBOL can be used to set up a command and control environment, which aligns perfectly with the triggered alert “Malware Command and Control Activity detected”.
Check the other web traffic.
1
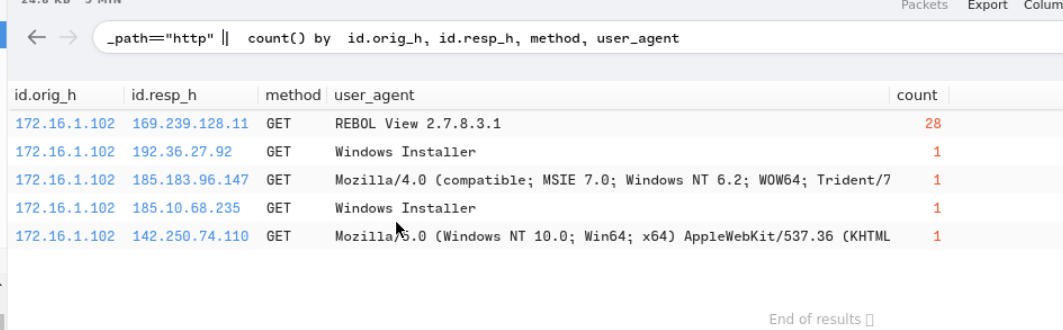
_path=="http" | count() by id.orig_h, id.resp_h, method, user_agent
Upon checking the two IP addresses that use Windows Installer as a user-agent in VirusTotal, they were flagged as malicious.
1
185[.]10[.]68[.]235,192[.]36[.]27[.]92
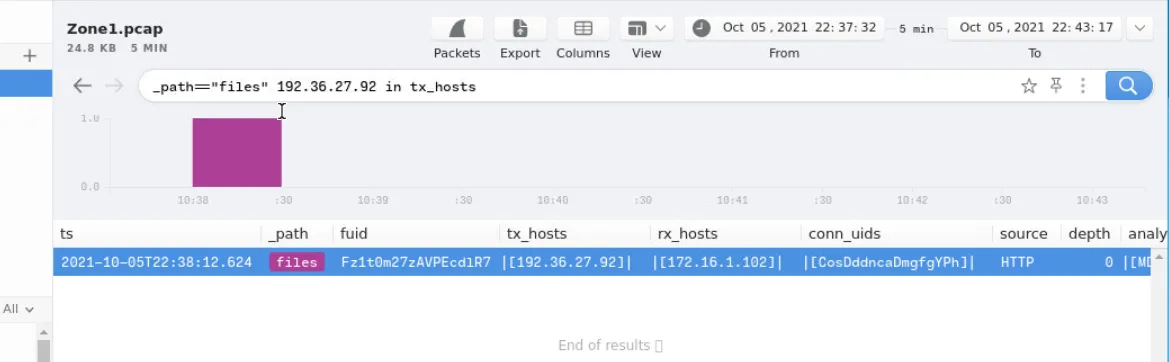
Check if there are any downloaded files from the Windows Installer user agent
1
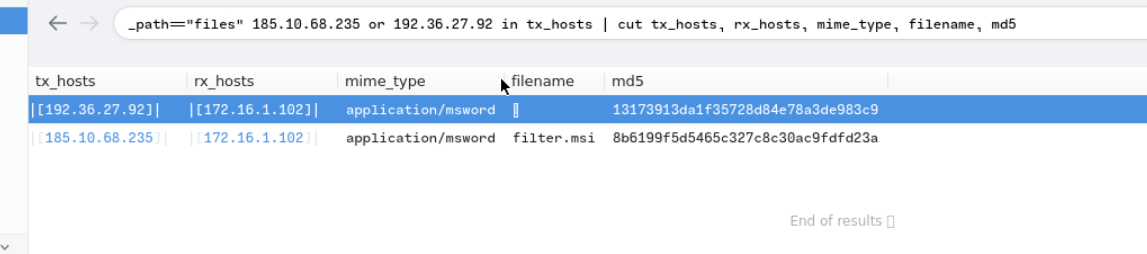
_path=="files" 185.10.68.235 or 192.36.27.92 in tx_hosts | cut tx_hosts, rx_hosts, mime_type, filename, md5
check the MD5 hash in Virustotal; both were flagged as malicious files
1
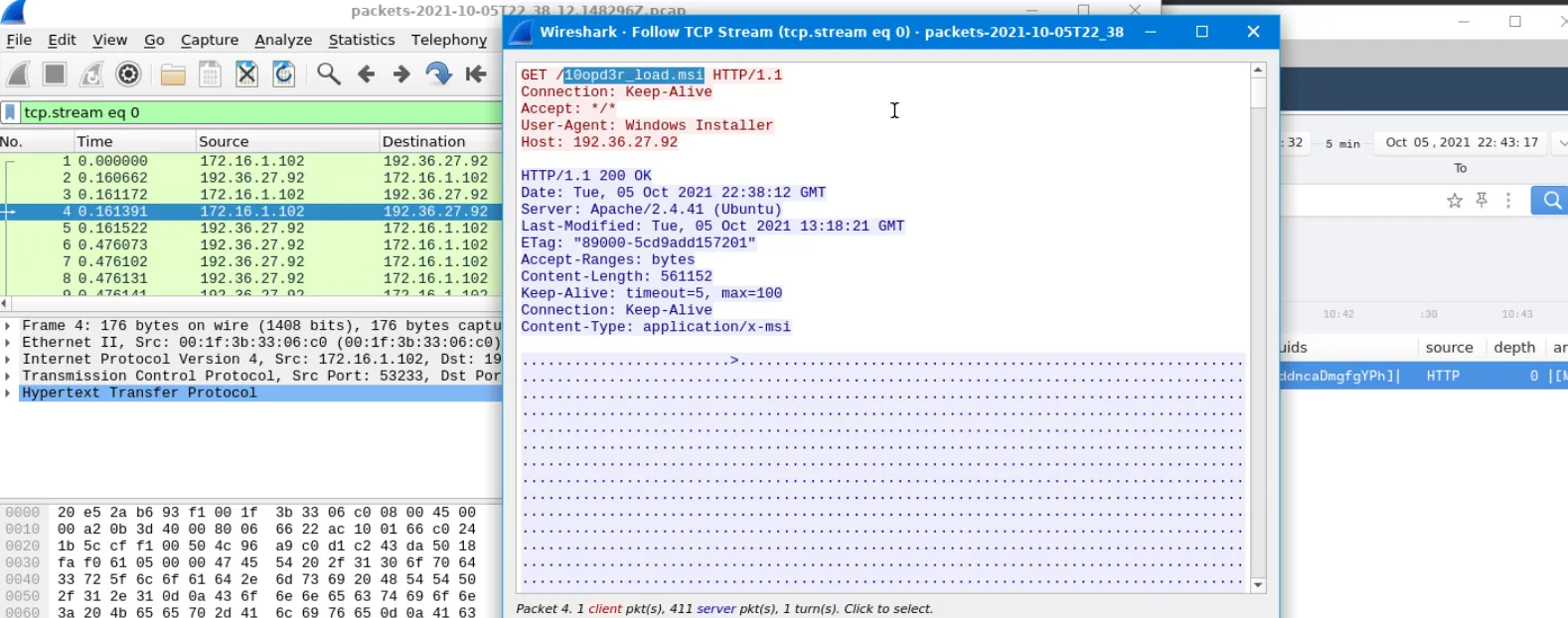
filter.msi,10opd3r_load.msi
To inspect the contents of the files, select the row you want to inspect, then click on the Packets tab, this will open Wireshark and list all the packets associated with this packet.
Select any packet and follow the stream
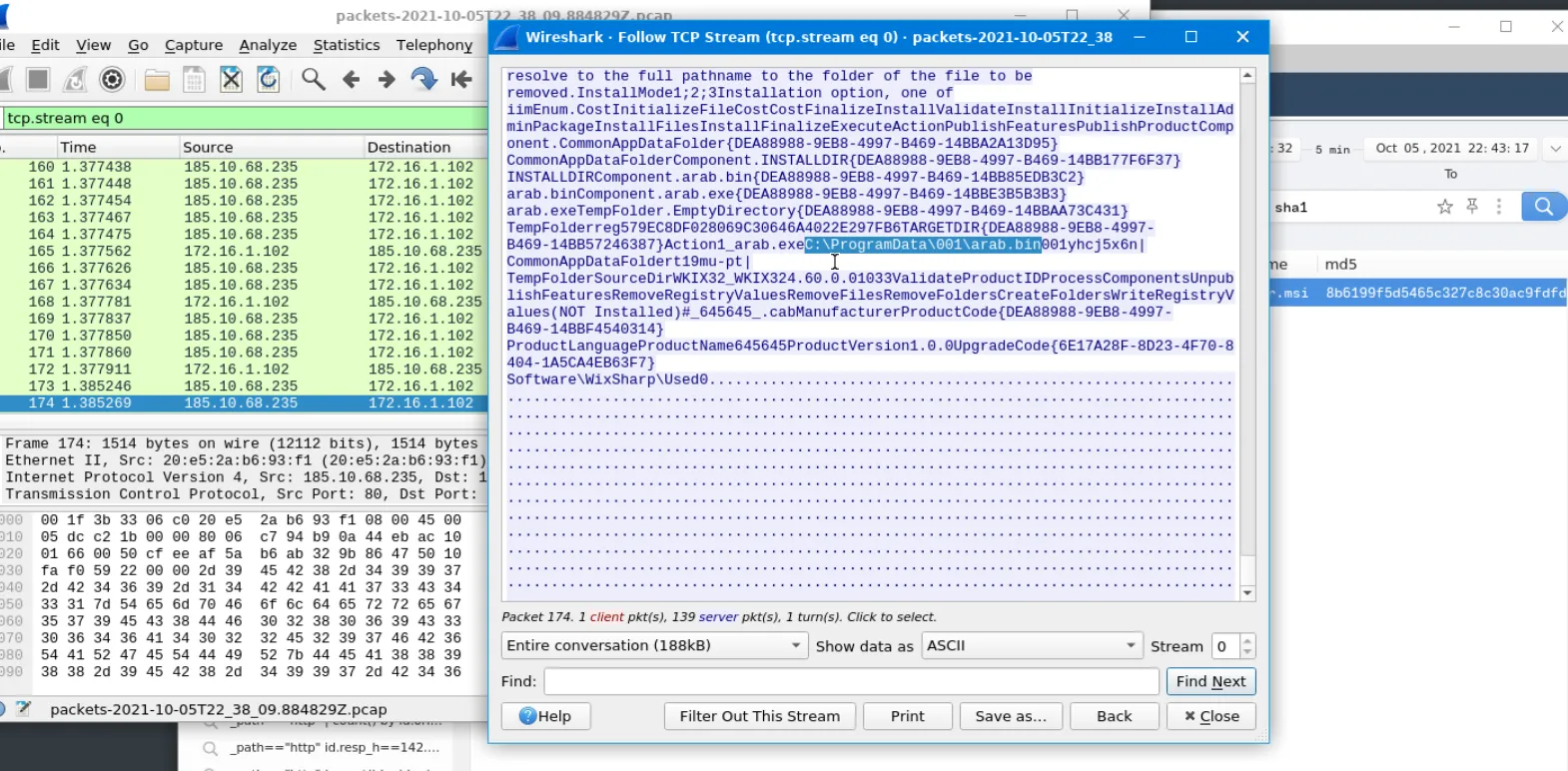
An MSI file is a relational database; each table defines a different aspect of the installation process. At the end of the content, you will see instructions that the Windows Installer service uses to install, update, or remove an application.
The file, filter.msi was designed to install arab.exe and arab.bin under this directory: C:\ProgramData\001\ , it also creates a registry entries under Software\WixSharp\Used
Do the same with the second file.
1
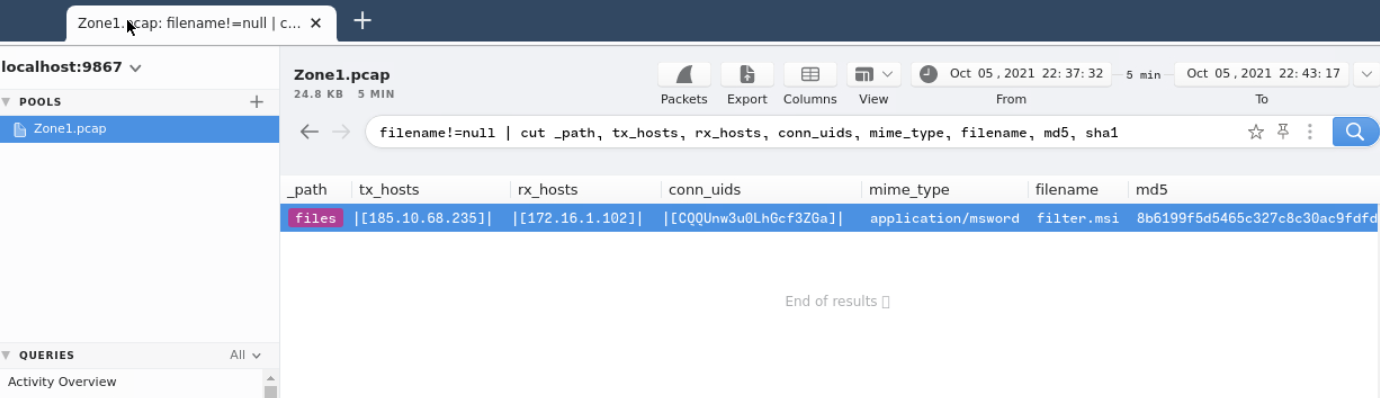
_path=="files" 192.36.27.92 in tx_hosts
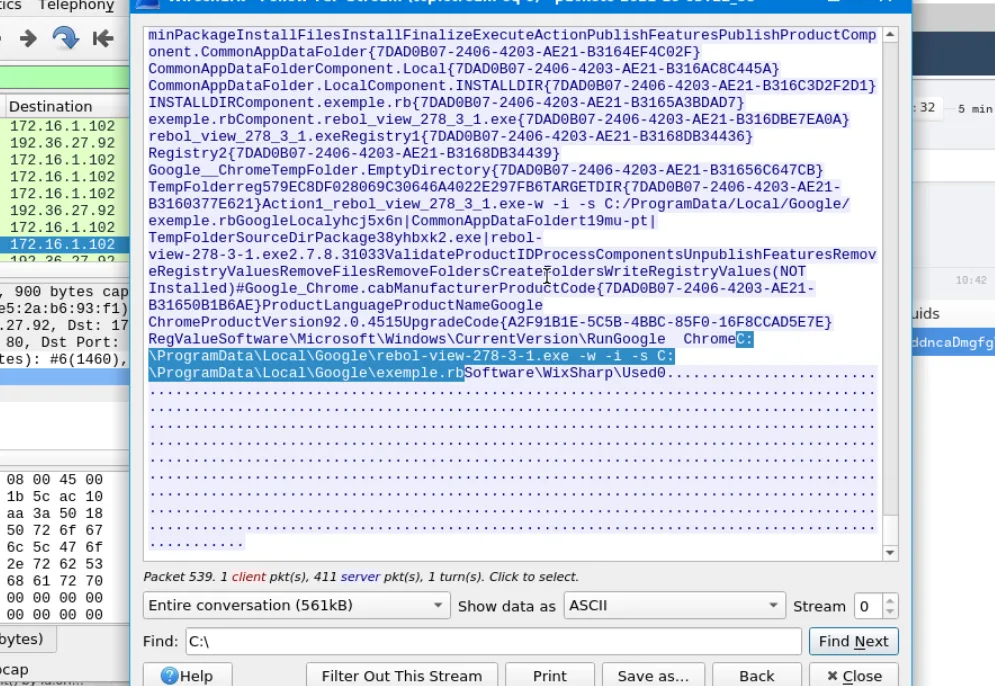
The second installer, 10opd3r_load.msi is used to fetch and set up the REBOL environment to execute a REBOL script named exemple.rb.
1
C:\ProgramData\Local\Google\rebol-view-278-3-1.exe,C:\ProgramData\Local\Google\exemple.rb
Conclusion
The analysis confirmed that the alert was a True Positive. We confirmed a multi-stage malware attack from the threat group TA505. The attack used malicious MSI files (filter.msi, 10opd3r_load.msi) to deploy a payload (arab.exe) and the REBOL framework to establish a stealthy command and control (C2) channel.
Check the next write-up for Warzone 2