TryHackMe: REloaded Write-up
Introduction
Challenge Link: REloaded
This room is dedicated for the RE challenges, each challenge has unique concepts divided in each binaries.
Level 0
This challenge is the most basic of RE. It will teach about how to enumerate files and get juicy details.
1
2
3
remnux@remnux:~/Downloads/REloaded/0$ wine Level-0_1610287551028.exe
Enter The Flag :: test
Dont Worry its a start ;)
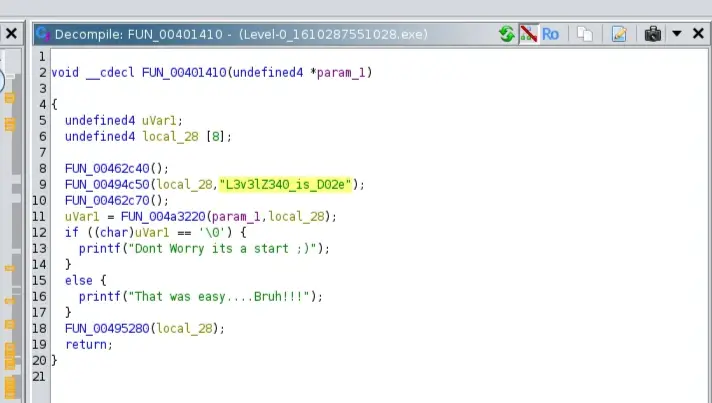
I searched for the string Dont Worry its a start ;) in the source code, and found this function
The function stores the expected key"L3v3lZ340_is_D02e" in local_28 then compare the user input (param_1) with the expected string via FUN_004a3220
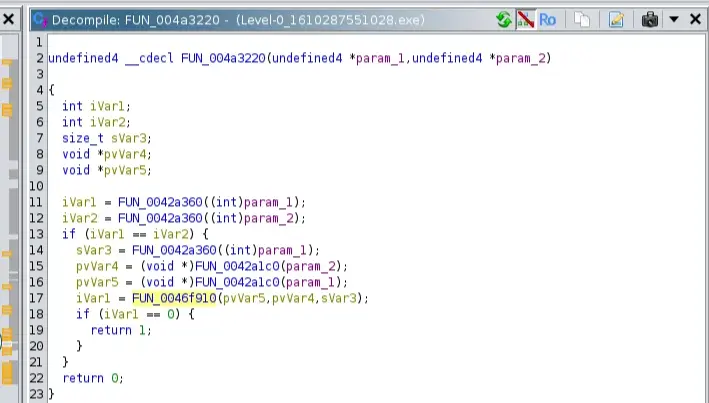
Double-click on FUN_004a3220 , it checks if the length of the two parameters is equal; if so, it will pass it to the function FUN_0046f910
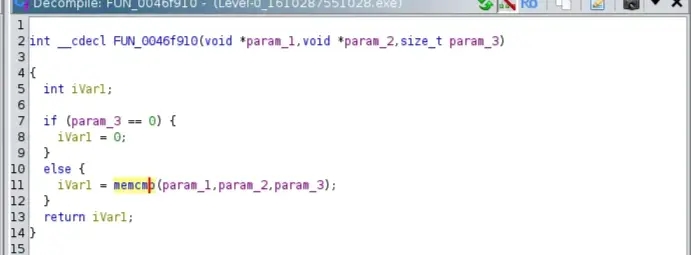
Navigating to the function FUN_0046f910 we see it uses memcmp() function that is used to compare two blocks of memory byte by byte. Syntax
1
int memcmp(const void *s1, const void *s2, size_t n);
So eventually, our input is compared against L3v3lZ340_is_D02e
1
2
3
remnux@remnux:~/Downloads/REloaded/0$ wine Level-0_1610287551028.exe
Enter The Flag :: L3v3lZ340_is_D02e
That was easy....Bruh!!!
Level 1
Level 0 was piece of cake for you now I am keeping my cake in the cage.
1
2
remnux@remnux:~/Downloads/REloaded/1$ wine Level-1_1610287698659.exe
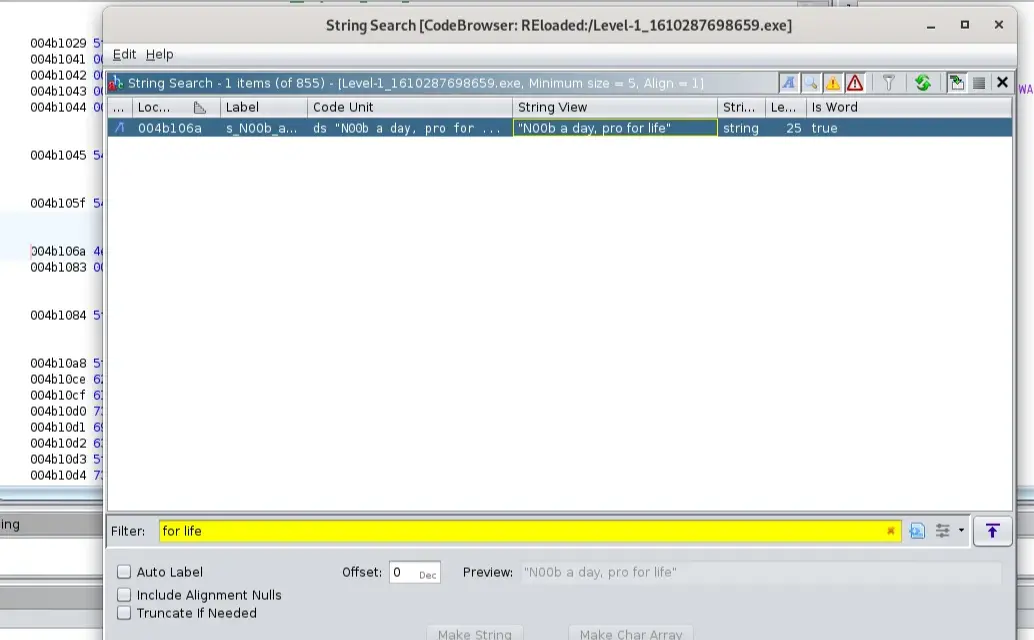
N00b a day, pro for life
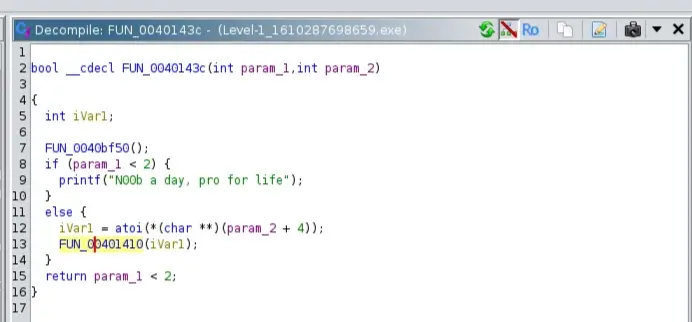
Searched for the printed string from Search > for string to start the search from the function printed this text
The function checks for the user input, if there is no passed argument, then it will print N00b a day, pro for life else, it will call the function FUN_0040141
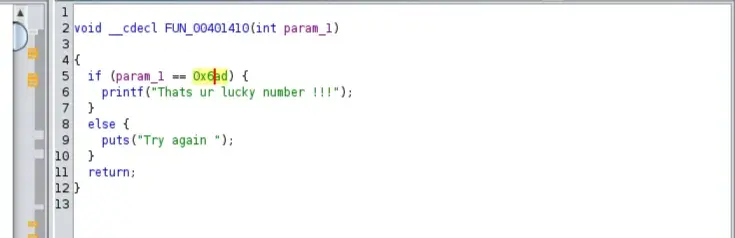
And here is the function that checks for the passed arguments; it checks if the value is equal to 0x6ad → 1709d
1
2
remnux@remnux:~/Downloads/REloaded/1$ wine Level-1_1610287698659.exe 1709
Thats ur lucky number !!!
Level 2
As a security analyst, you found some suspicious app in your organization which enables employees secretly share their file to the rival organization. Your task is to find who is involved in this treachery, but the app needs some key to log in. Can you patch this app to bypass Authentication?
1
2
3
4
remnux@remnux:~/Downloads/REloaded/2$ wine Level-2_1610288072323.exe
Wow Ur At L3?
remnux@remnux:~/Downloads/REloaded/2$ wine Level-2_1610288072323.exe test
In order to advance you have to break your mindset
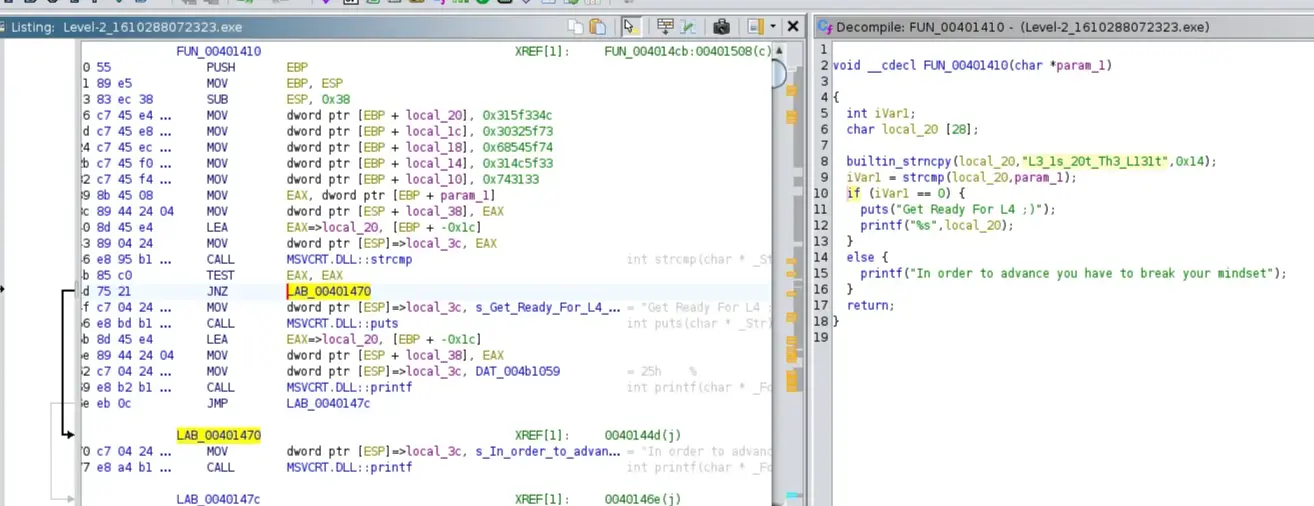
Navigating to the function that prints the output, we see that it uses the function strncpy()
The strncpy() function in C is used to copy a specified number of characters from a source string to a destination string. Syntax
1
char *strncpy(char *dest, const char *src, size_t n);
So in the code, it copied the string “L3_1s_20t_Th3_L131t” to local_20 size of 14h, then it used strcmp() function to compare the string saved in local_20 to our input.
1
2
3
remnux@remnux:~/Downloads/REloaded/2$ wine Level-2_1610288072323.exe L3_1s_20t_Th3_L131t
Get Ready For L4 ;)
L3_1s_20t_Th3_L131t
And the instruction we modified in the assembly code is JNZ(jump if not zero), if the string matches, it will print success; otherwise, it will jump to LAB_00401470 and print In order to advance you have to break your mindset
Level 3
Bob was fired due to his inappropriate behavior with colleagues. While leaving he deleted the code which decrypts the password stored in the code. As a reverse engineer it’s your task to recover that master password since the code is in prod now and cant is modified but you have a copy of the app. everything depends on you now !!!
1
2
3
remnux@remnux:~/Downloads/REloaded/3$ wine Level-3_1610295976945.exe
Enter the flag ::test
-_-
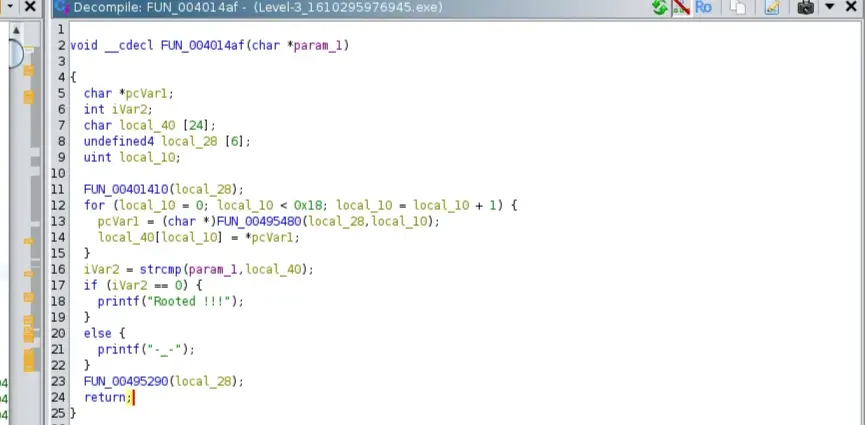
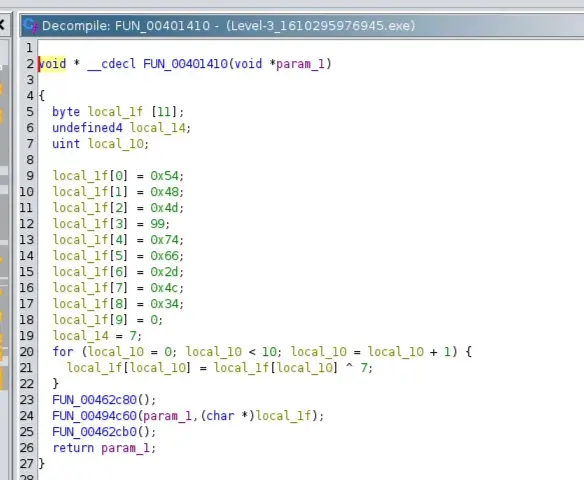
Here is the function that compares our string with the password
FUN_004014af builds a 24-byte buffer local_40 by calling FUN_00401410 to prepare some data in local_28, then copying 24 characters (indices 0..0x17) from that prepared data into local_40. After that it compares the user-provided string param_1 to local_40 with strcmp() and prints "Rooted !!!" if they match, otherwise "-_-". Finally it calls FUN_00495290(local_28) to clean up.
Here is the function that stores the password
The function stores each byte in local_1f then loops each byte and modifies it by XORing it with the number 7at runtime.. HexToStringConverter
Level 4
They are back!!! and using some sort of encryption algorithm to communicate. Although we intercepted their messages we cant decode them, Agent 35711 has successfully stolen their test encryption code. Now it’s on you to build a decryptor for test messages and save this world.
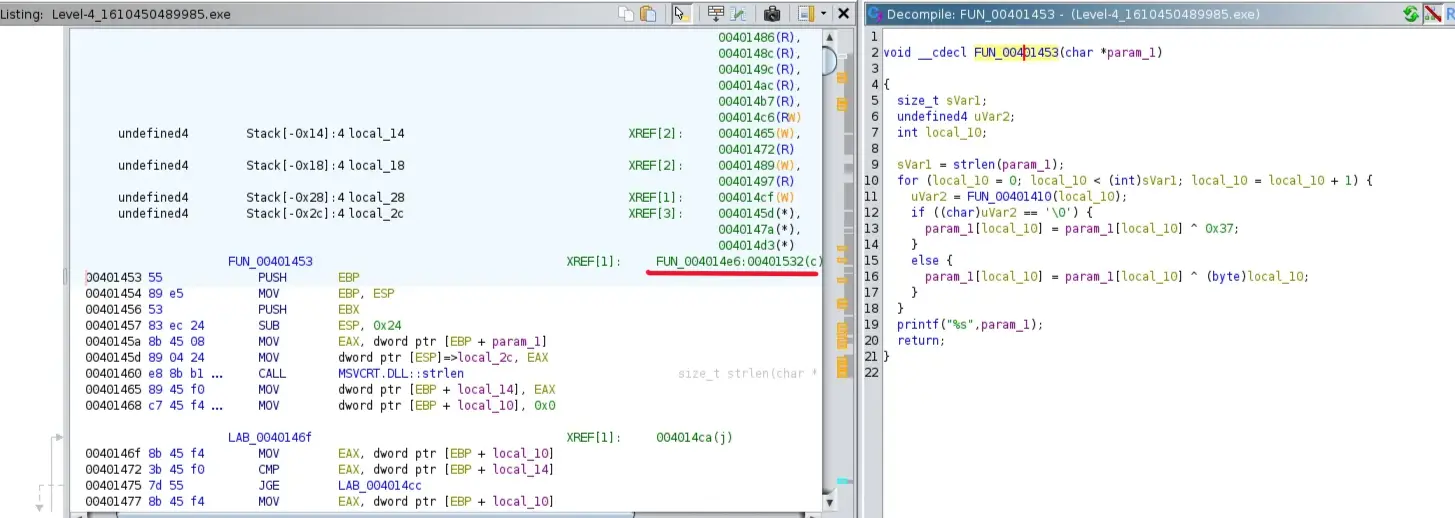
If you run the program, it will print a random string, so instead of searching for these strings, search for the function that printed that output, and in this source code, it is the printf() function
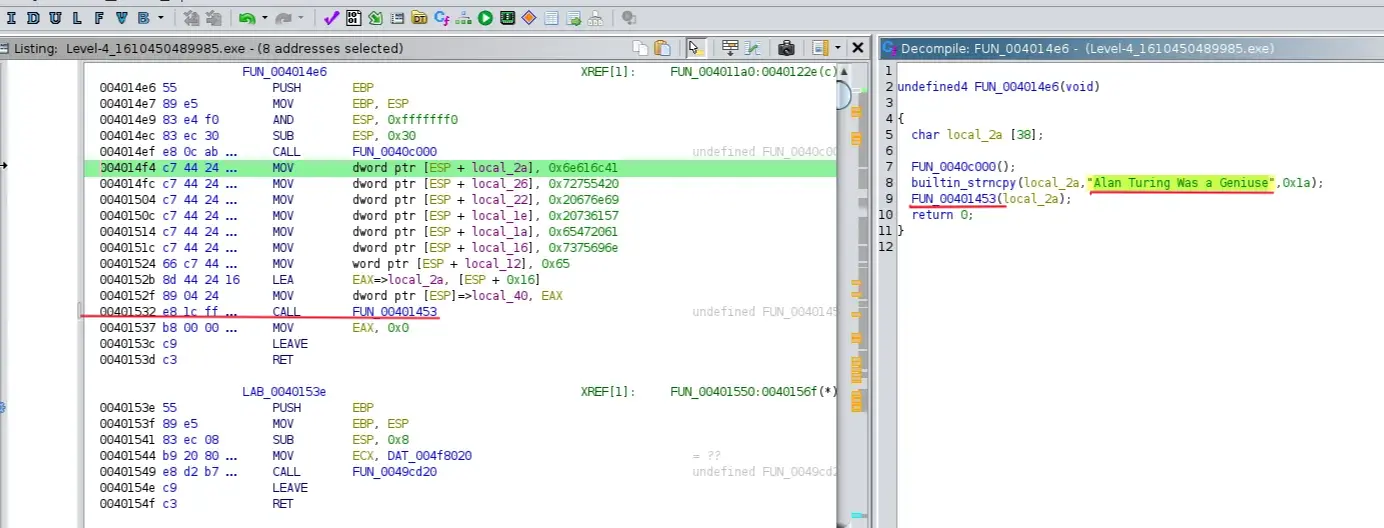
The function loops through each character of the input string, if FUN_00401410(i) returns 0 → it XORs the character with 0x37otherwise it XORs the character with its index i then it print the transformed string. The function has one cross-reference to FUN_004014e6 at the address 00401532. Double-clicking on it, and you will see that the function uses strncpy() function to copy the string “Alan …” into local_2a, then call the above funciton FUN_00401453on it