CyberDefenders: Insider Write-up
Introduction
Challenge Link: Insider
Analysis Linux artifacts, including logs and Bash history, using FTK Imager to investigate insider threat activities and reconstruct user actions.
- Download FTK imager from exterro ftk-imager-4-7-3-81)
Scenario
After Karen started working for ‘TAAUSAI,’ she began doing illegal activities inside the company. ‘TAAUSAI’ hired you as a soc analyst to kick off an investigation on this case. You acquired a disk image and found that Karen uses Linux OS on her machine. Analyze the disk image of Karen’s computer and answer the provided questions.
Q&A
Q1. Which Linux distribution is being used on this machine?
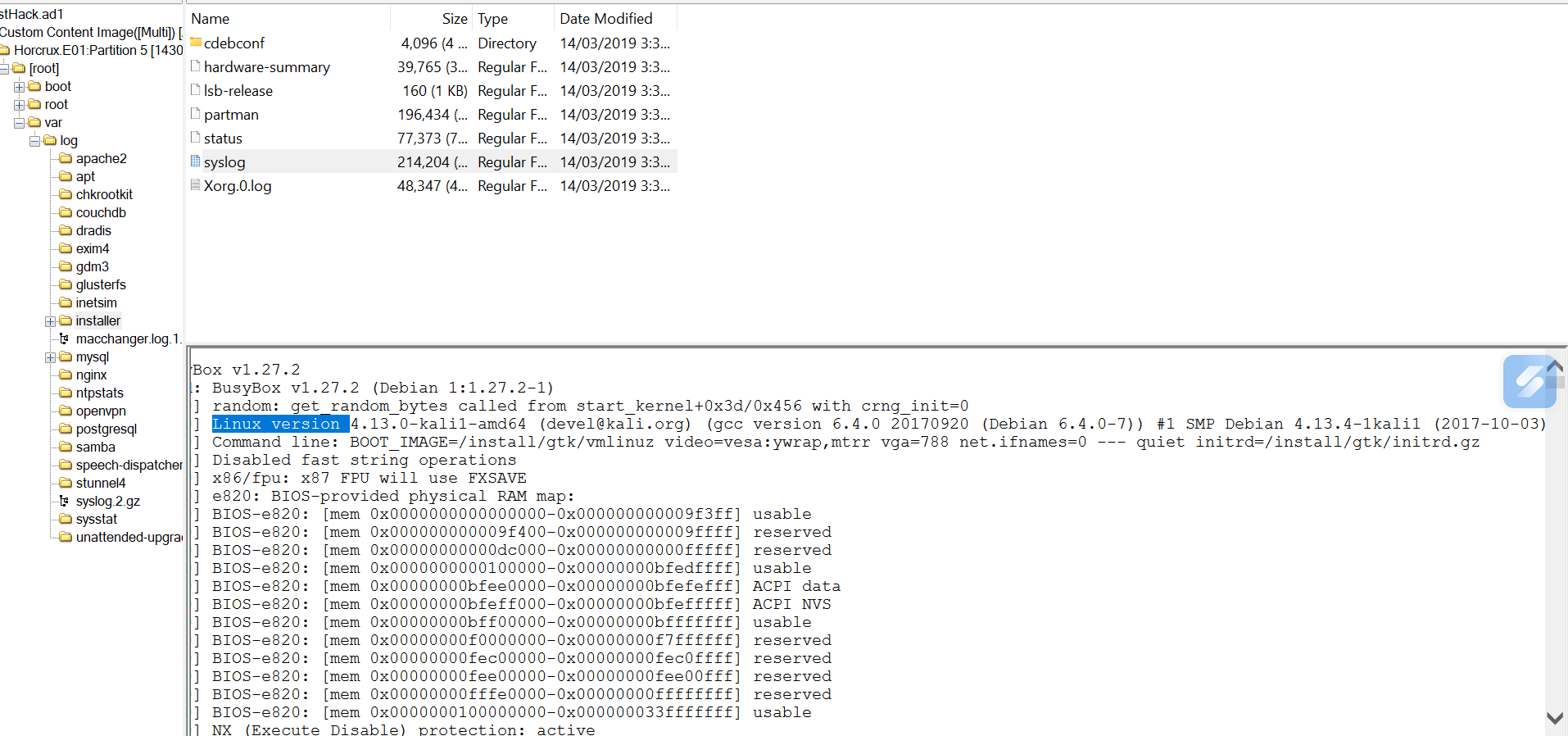
Navigate to the logs or configuration files that can reveal system information, such as the syslog file, which logs system activities, error states, and security events. This file is located at var>log>installer>syslog
In the syslog, we found a line revealing the system information
1
2
Linux version 4.13.0-kali1-amd64 (devel@kali.org) (gcc version 6.4.0 20170920 (Debian 6.4.0-7)) #1 SMP Debian 4.13.4-1kali1 (2017-10-03)
This line confirms that the operating system is Kali Linux, a Debian-based distribution, and the kernel version is 4.13.4-1kali1 compiled using the GCC version 6.4.0. The reference to kali.org confirms the distribution as Kali Linux.
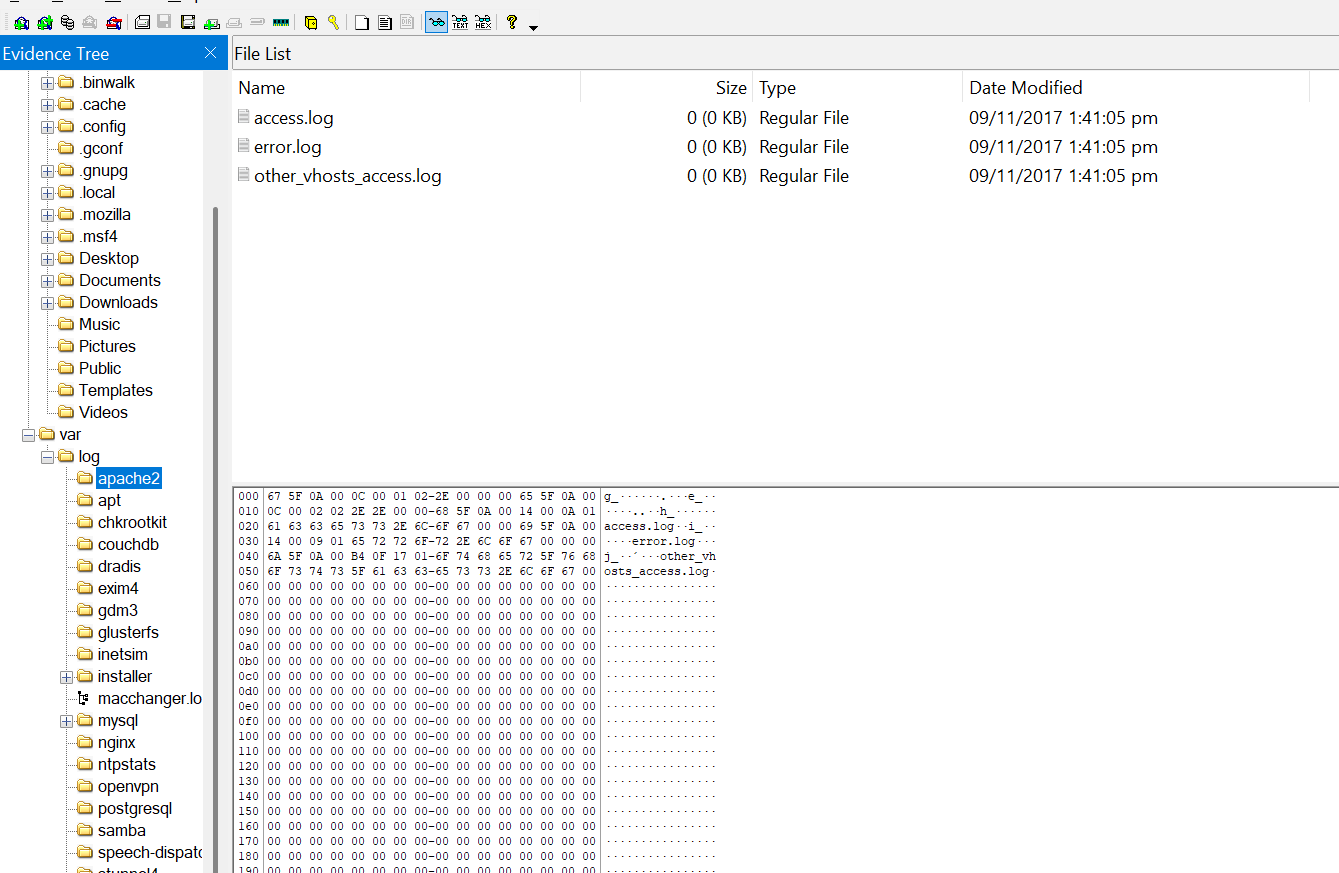
Q2. The Apache logs are typically located in /var/log/apache2/. Once you find the access log, you can calculate its MD5 hash.
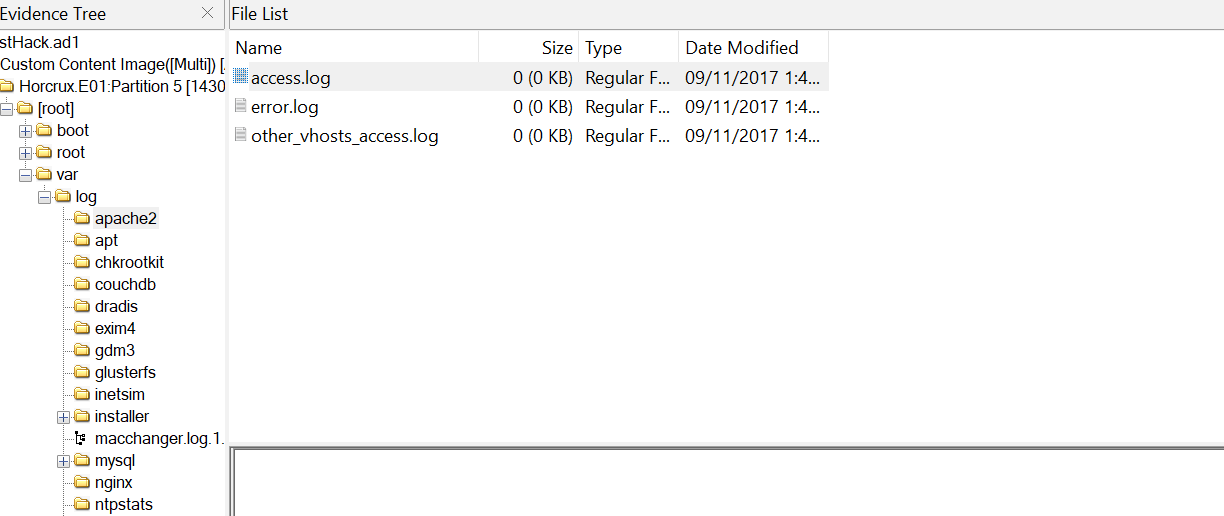
The Apache logs in linux system is used to monitor web server activity. The primary log files are the access.log and error.log
- access.log → records all requests processed by the apache web server, including client IPs, requested URL, HTTP status code, and more.
- error.log → Contains information about errors, warnings, and other anomalies encountered by Apache
To calculate the MD5 hash of the access.log file, navigate to the Apache2 folder found under var>log>apache2 and right-click on the access.log and select Export Files or export file hash.
If you exported the files, calculate the MD5 hash of the saved file.
1
2
3
4
5
6
Get-FileHash -Algorithm MD5 "access.log"
Algorithm Hash Path
--------- ---- ----
MD5 D41D8CD98F00B204E9800998ECF8427E
Q3. It is suspected that a credential dumping tool was downloaded. What is the name of the downloaded file?
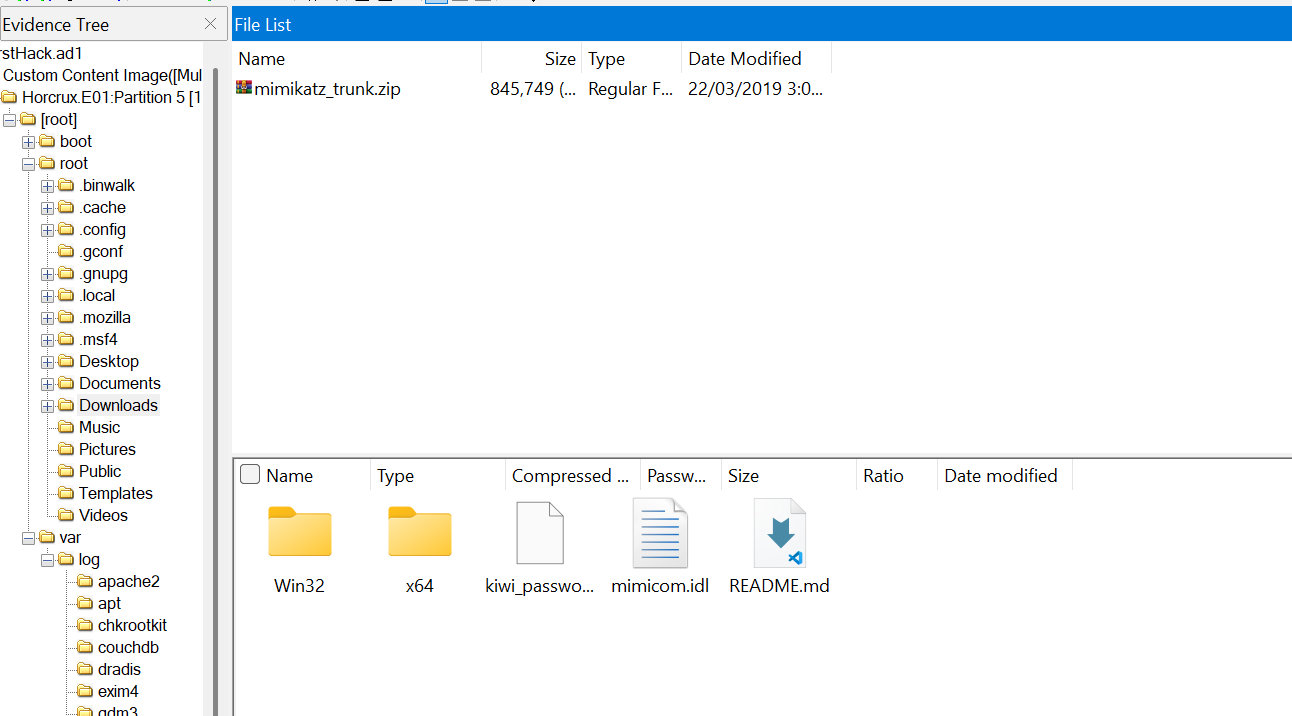
Navigate to the Downloads folder under the root directory. You will find an archive file called mimikatz
Mimikatz is an open-source tool used for port-exploitation attacks. Mimikatz can perform credential-gathering techniques such as:
- Pass-the-hash
- Pass-the-ticket
- Overpass-the-hash (pass-the-key)
- Kerberoast golden tickets
- Kerberoast silver tickets
- Pass-the-cache
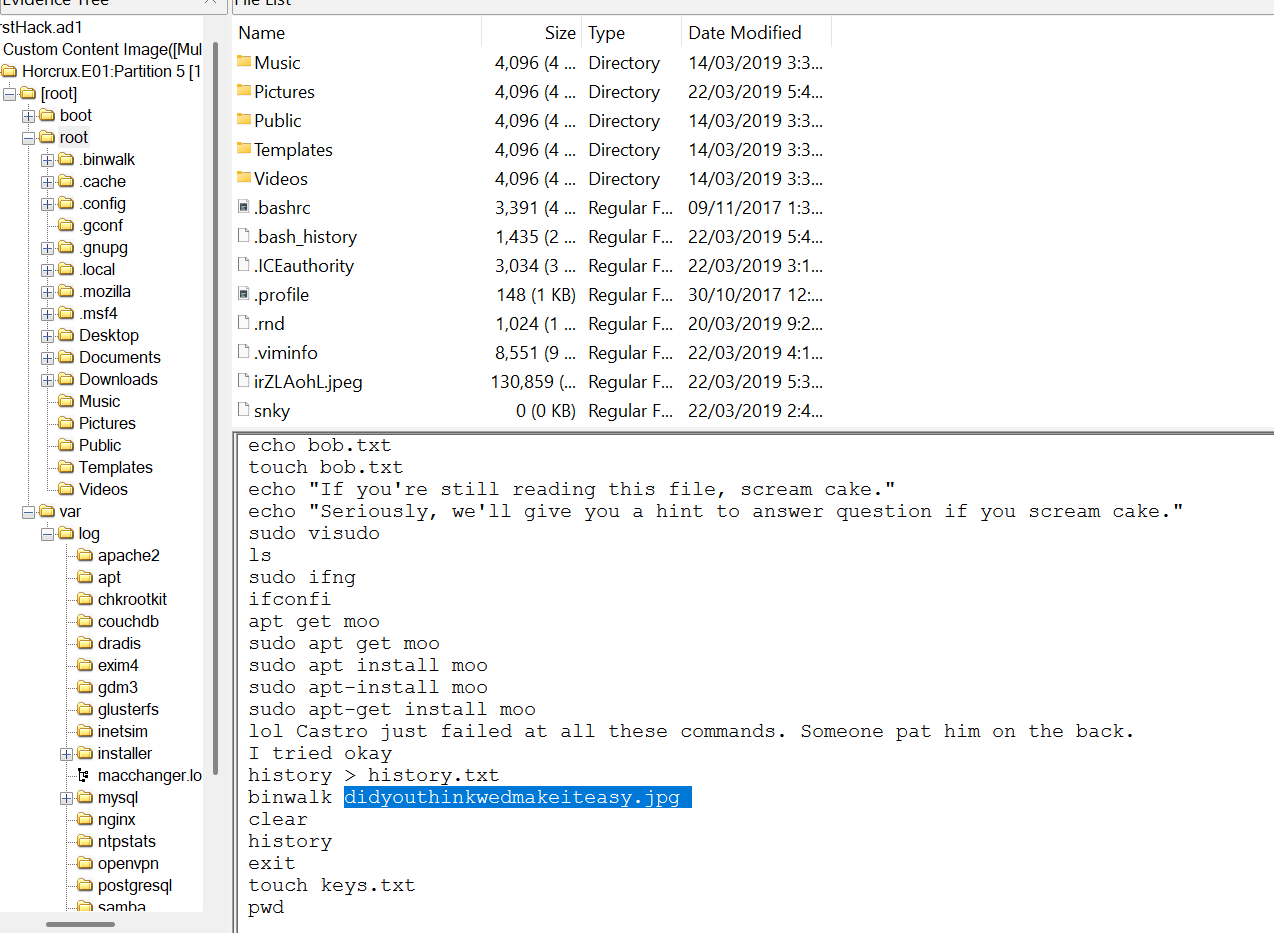
Q4. A super-secret file was created. What is the absolute path to this file? in the bash_history
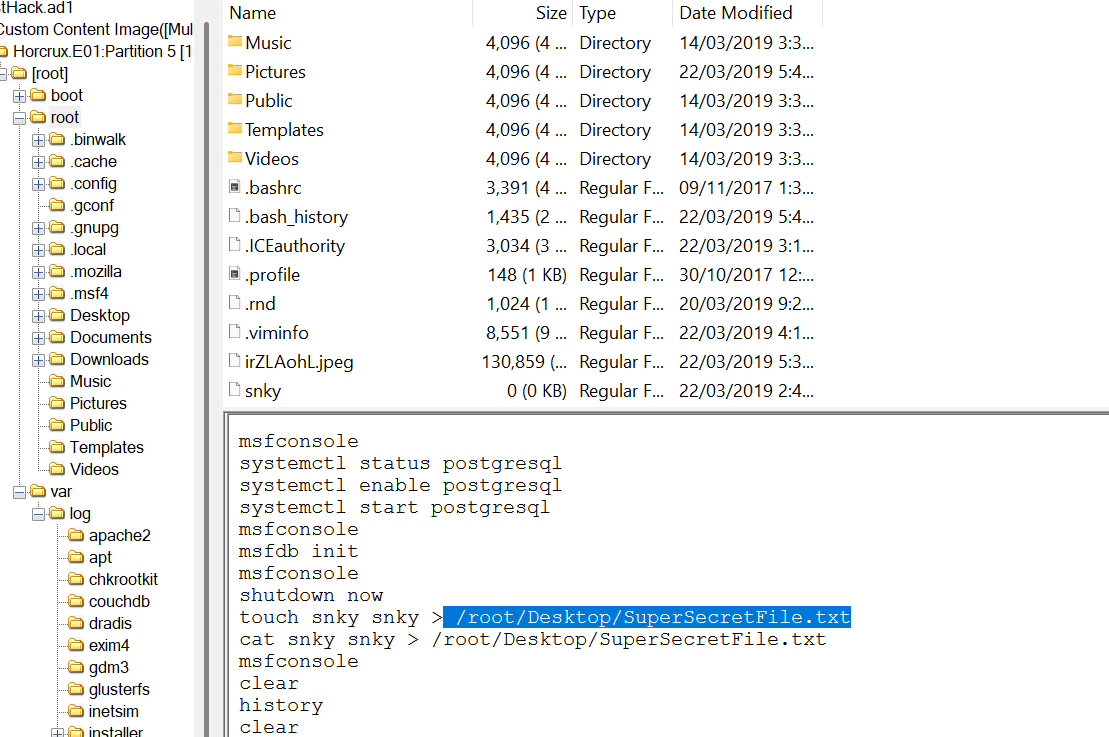
Under each user account, there is a file that logs all the executed commands in the terminal, the bash_history
In the bash_history log, we can see that the user “root” is creating a file named SuperSecretFile.txt in the /root/Desktop directory.
Q5. What program used the file didyouthinkwedmakeiteasy.jpg during its execution?
In the bash_history log, there is a command showing binwalk being used on didyouthinkwedmakeiteasy.jpg. Binwalk is a forensics tool used to inspect images, executables, and other binary data for hidden payloads or embedded code.
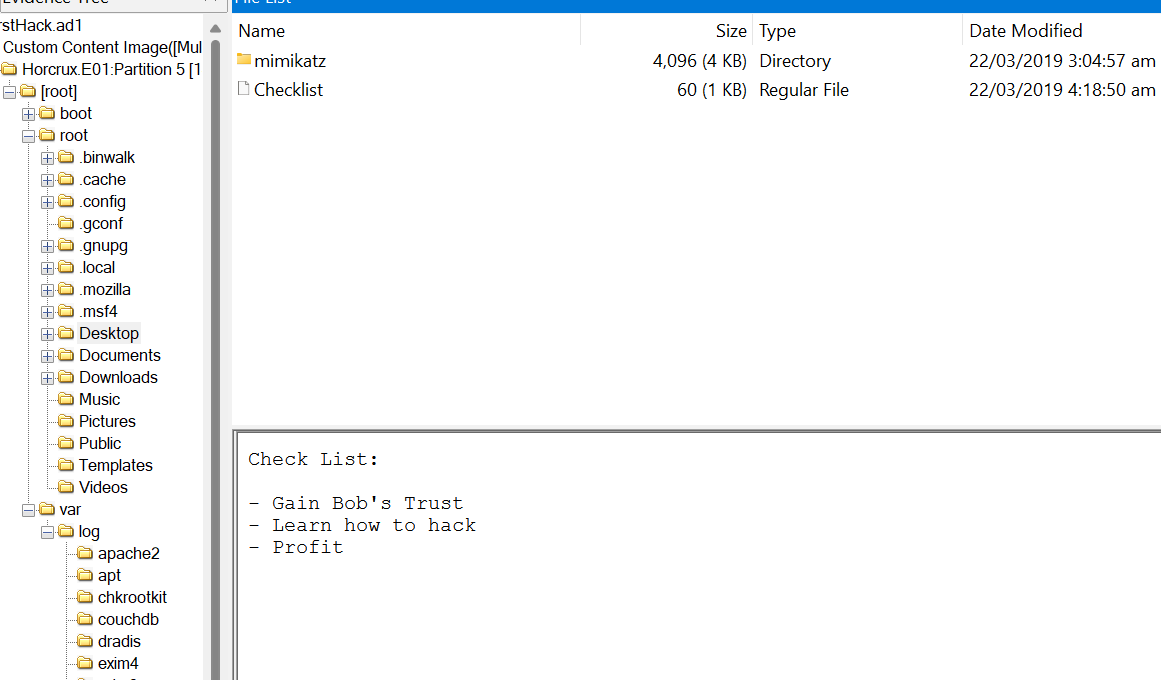
Q6. What is the third goal from the checklist Karen created?
A common location to save the user’s notes, such as checklists, is in the Desktop. Navigate to the Desktop directory, and you will find a file named Checklist that contains several goals to achieve, and the last goal is Profit.
Q7. How many times was Apache run?
All three logs in the Apache folder are empty; no data has been recorded in these logs.
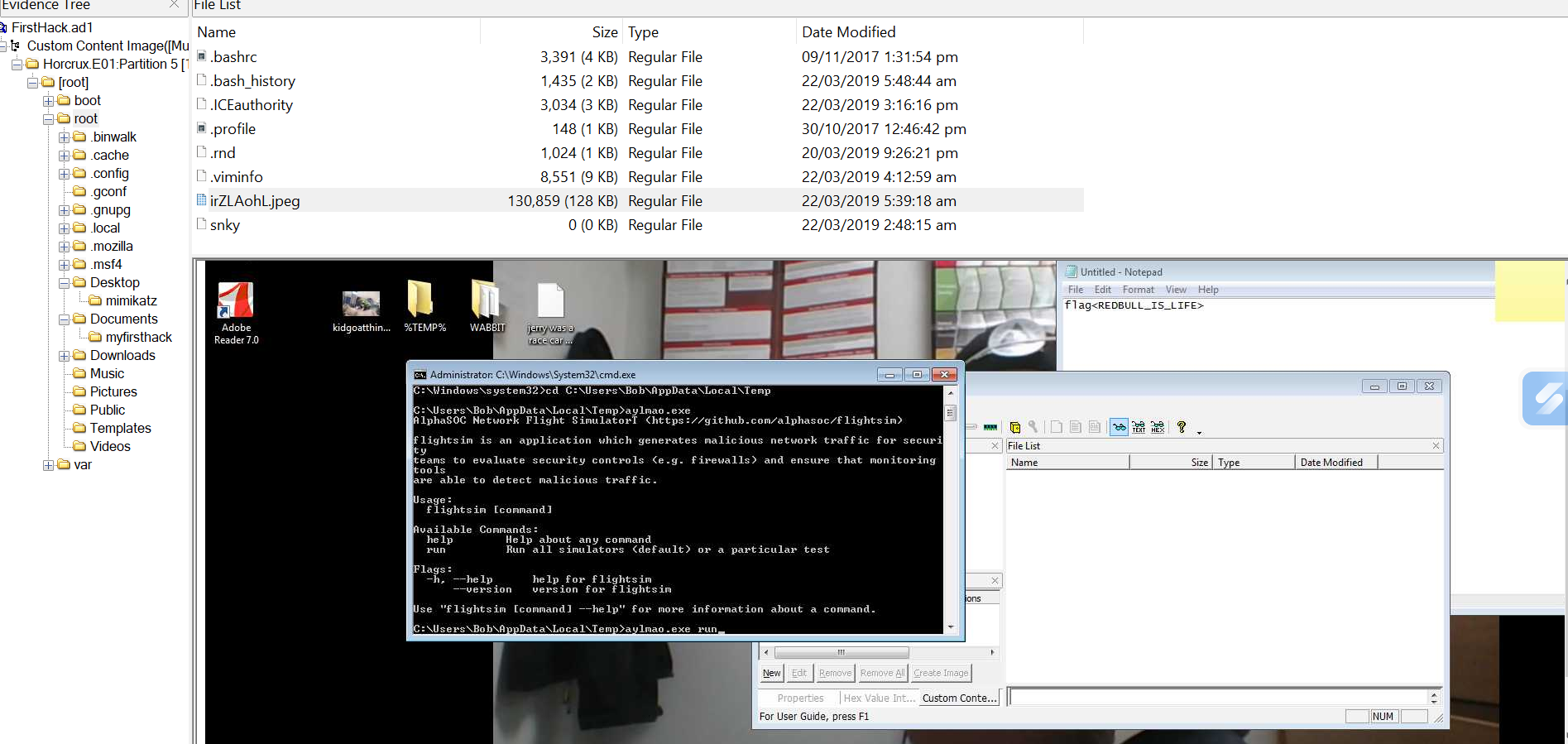
Q8. This machine was used to launch an attack on another. Which file contains the evidence for this?
When inspecting the root directory, I stumbled upon an image file displaying a Windows desktop with a terminal execution of the FlighSim tool.
FlighSim is a tool used to generate a malicious network traffic to simulate attacks, such as simulating DNS tunneling, DGA traffic, requests to known active C2 destinations, and other suspicious traffic patterns.
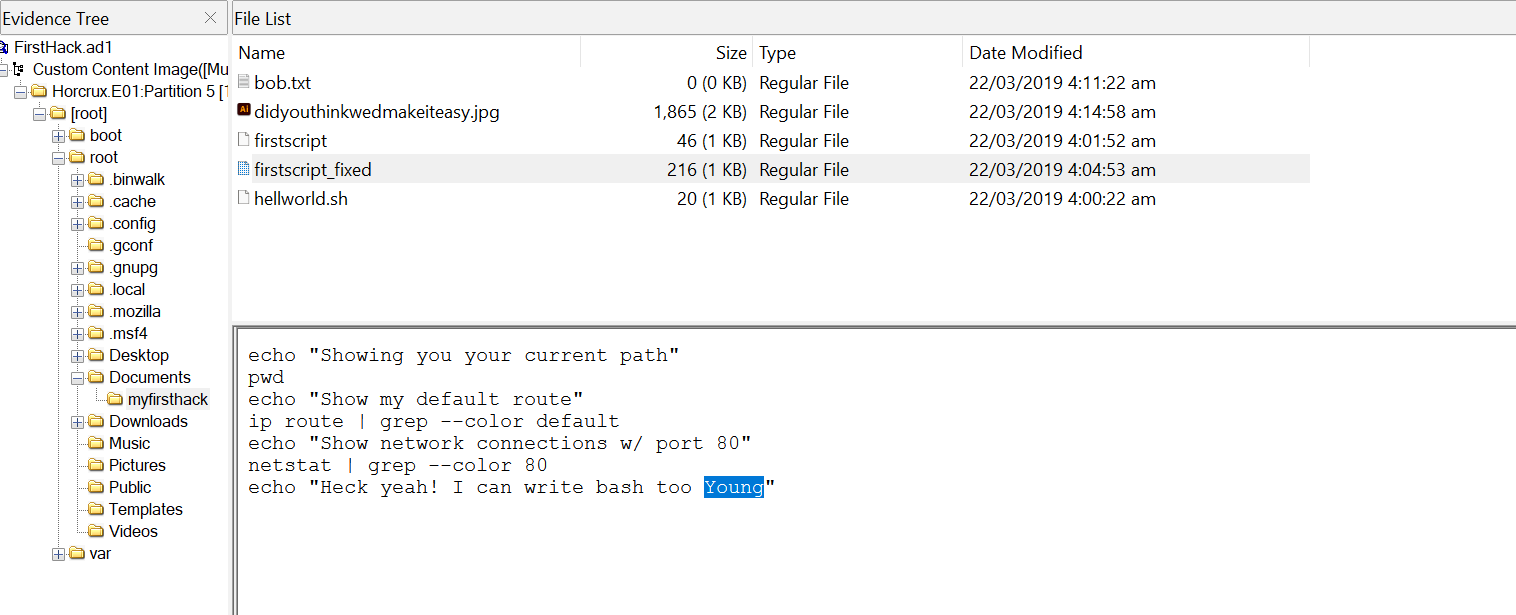
Q9. It is believed that Karen was taunting a fellow computer expert through a bash script within the Documents directory. Who was the expert that Karen was taunting?
In the Documents directory, there is a bash file named firstscript_fixed, which contains a shell script that will execute upon executing the file.
Its content shows that the user who created it was showing off technical skills to Young.
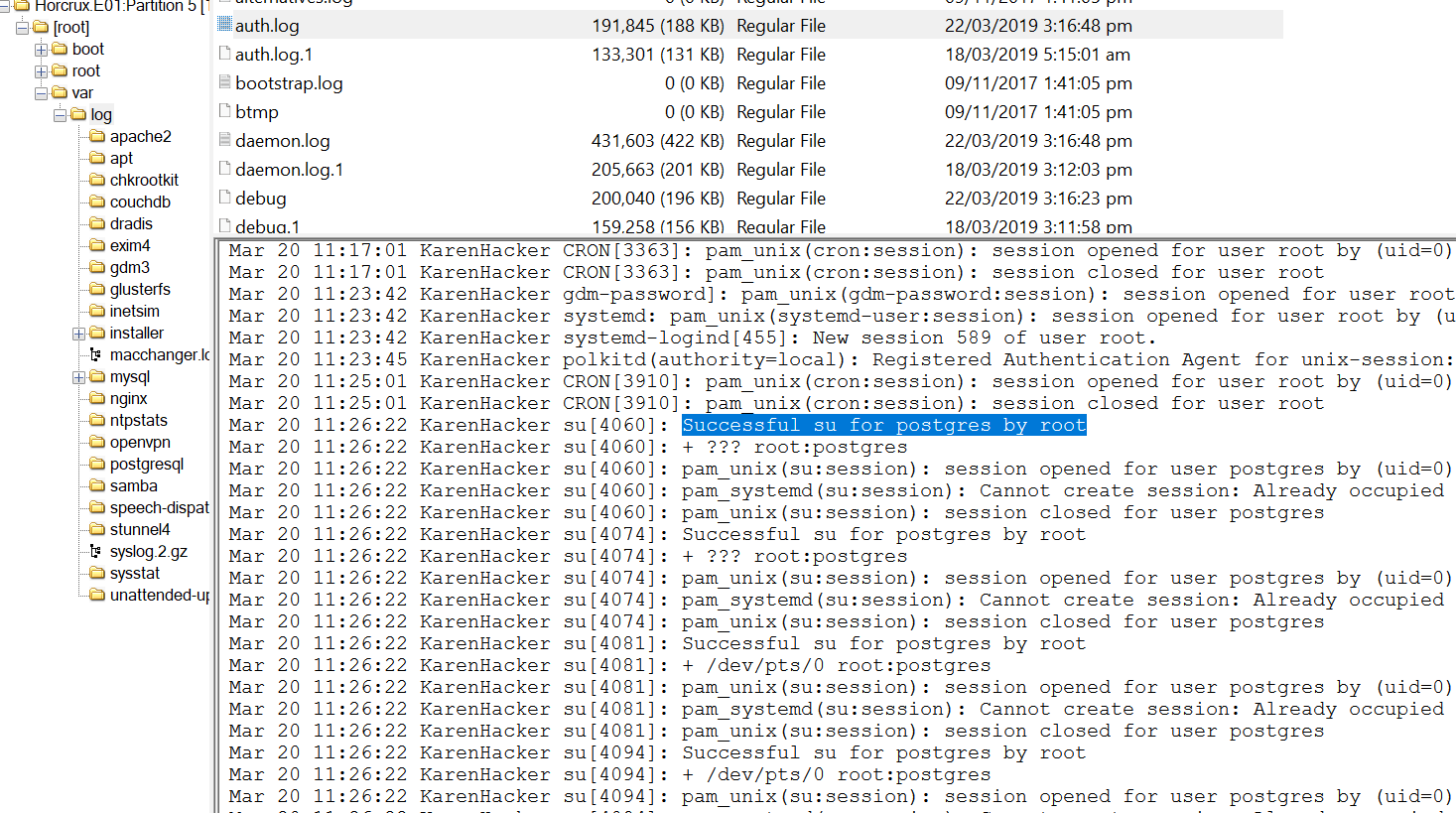
Q10. A user executed the su command to gain root access multiple times at 11:26. Who was the user?
The authentication logs record events related to user authentication and authorization. The authentication log is located at /var/log/auth.log . Based on the specified time, search for the execution of the su command.
1
2
Mar 20 11:26:22 KarenHacker su[4060]: Successful su for postgres by root
This line entry shows that on Mar 20, 11:26, the user KarenHacker switched to the postgres account using root privilege.
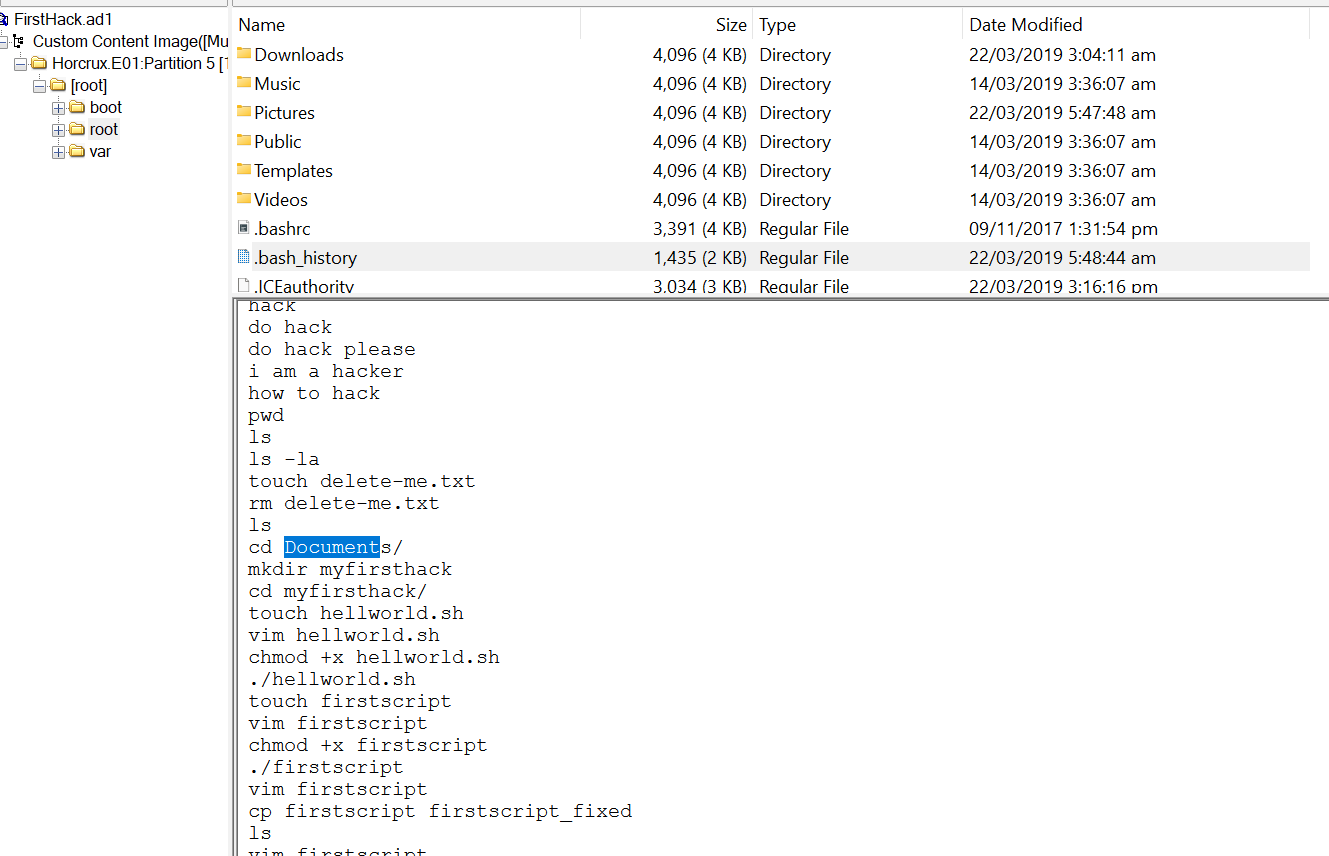
Q11.Based on the bash history, what is the current working directory?
Based on the execution of the cdcommand in the bash_history file, the user was in the root directory, then switched to the Documents, created a directory named myfirsthack, then moved to the newly created directory.
The absolute path is /root/Documents/myfirsthack/