TryHackMe: Cicada-3301 Vol:1 Write-up
Introduction
Challenge Link: Cicada3301vol1
A basic steganography and cryptography challenge room based on the Cicada 3301 challenges
Analyze the Audio
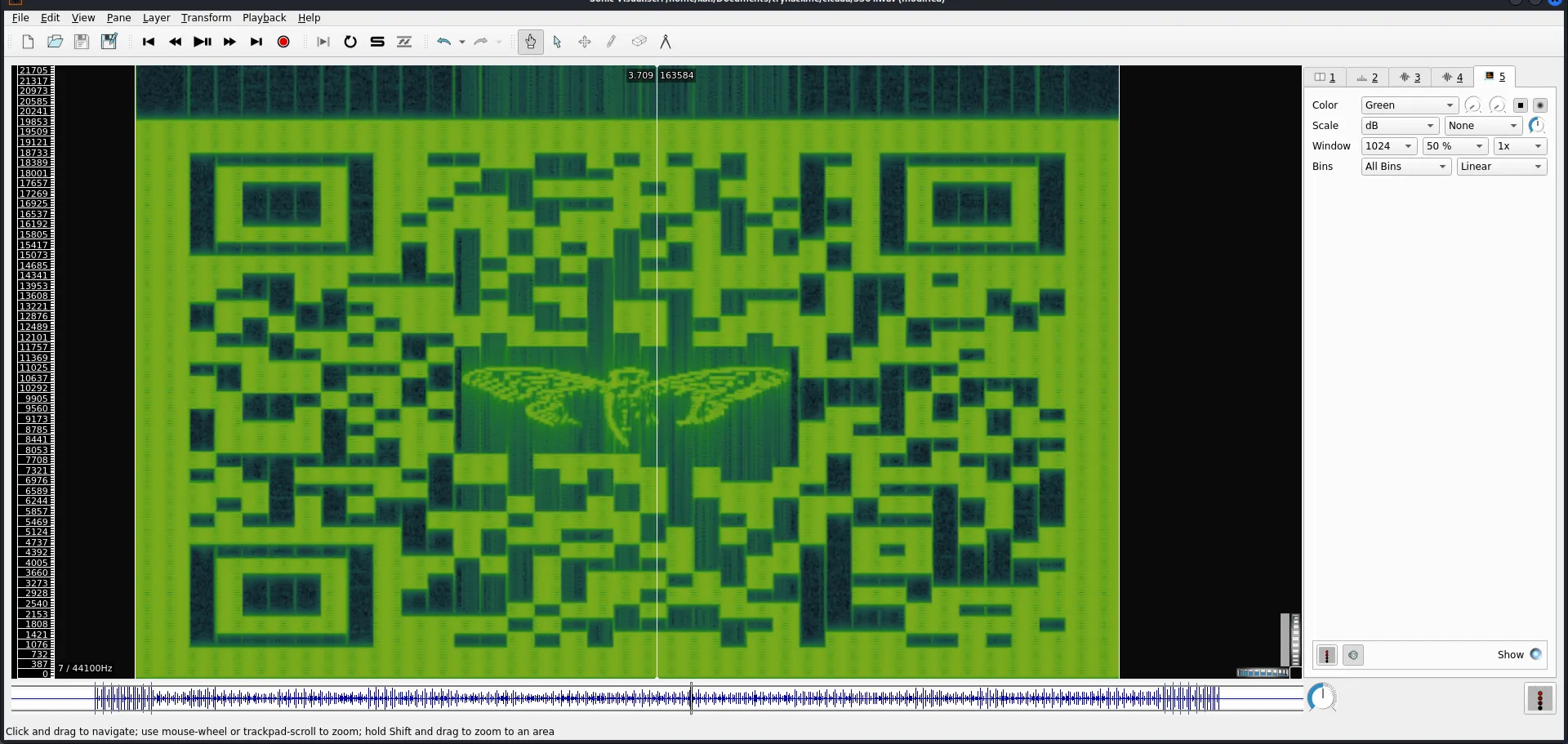
Use Sonic Visualizer to analyze the audio
Download the files:
1
2
3
4
unzip Cicada_3301_1586991734089.zip
Archive: Cicada_3301_1586991734089.zip
inflating: 3301.wav
inflating: welcome.jpg
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
file 3301.wav
3301.wav: RIFF (little-endian) data, WAVE audio, Microsoft PCM, 16 bit, mono 44100 Hz
┌──(kali㉿kali)-[~/Documents/tryhackme/cicada]
└─$ exiftool 3301.wav
ExifTool Version Number : 12.57
File Name : 3301.wav
Directory : .
File Size : 617 kB
File Modification Date/Time : 2020:04:15 01:59:42+03:00
File Access Date/Time : 2025:09:13 10:43:19+03:00
File Inode Change Date/Time : 2025:09:13 10:42:10+03:00
File Permissions : -rw-rw-r--
File Type : WAV
File Type Extension : wav
MIME Type : audio/x-wav
Encoding : Microsoft PCM
Num Channels : 1
Sample Rate : 44100
Avg Bytes Per Sec : 88200
Bits Per Sample : 16
Duration : 7.00 s
┌──(kali㉿kali)-[~/Documents/tryhackme/cicada]
└─$ xxd 3301.wav | head
00000000: 5249 4646 dc6b 0900 5741 5645 666d 7420 RIFF.k..WAVEfmt
00000010: 1000 0000 0100 0100 44ac 0000 8858 0100 ........D....X..
00000020: 0200 1000 6461 7461 b86b 0900 ff7f 3e0c ....data.k....>.
00000030: 7df3 e90a 67f5 8008 31f8 7605 59fb 5502 }...g...1.v.Y.U.
00000040: 52fe a4ff a300 c4fd 0502 e5fc 6302 fdfc R...........c...
00000050: e501 cefd da00 fbfe a4ff 2200 9ffe f400 ..........".....
00000060: 0cfe 4201 04fe 0a01 75fe 6c00 31ff a4ff ..B.....u.l.1...
00000070: f6ff f1fe 8b00 84fe c900 76fe a800 c3fe ..........v.....
00000080: 3800 4bff a5ff e0ff 1bff 5400 c5fe 8700 8.K.......T.....
00000090: b6fe 7000 f0fe 1b00 5bff a6ff d2ff 36ff ..p.....[.....6.
As the challenge description says, use sonic visualizer and add a spectrogram layer to view the hidden image.
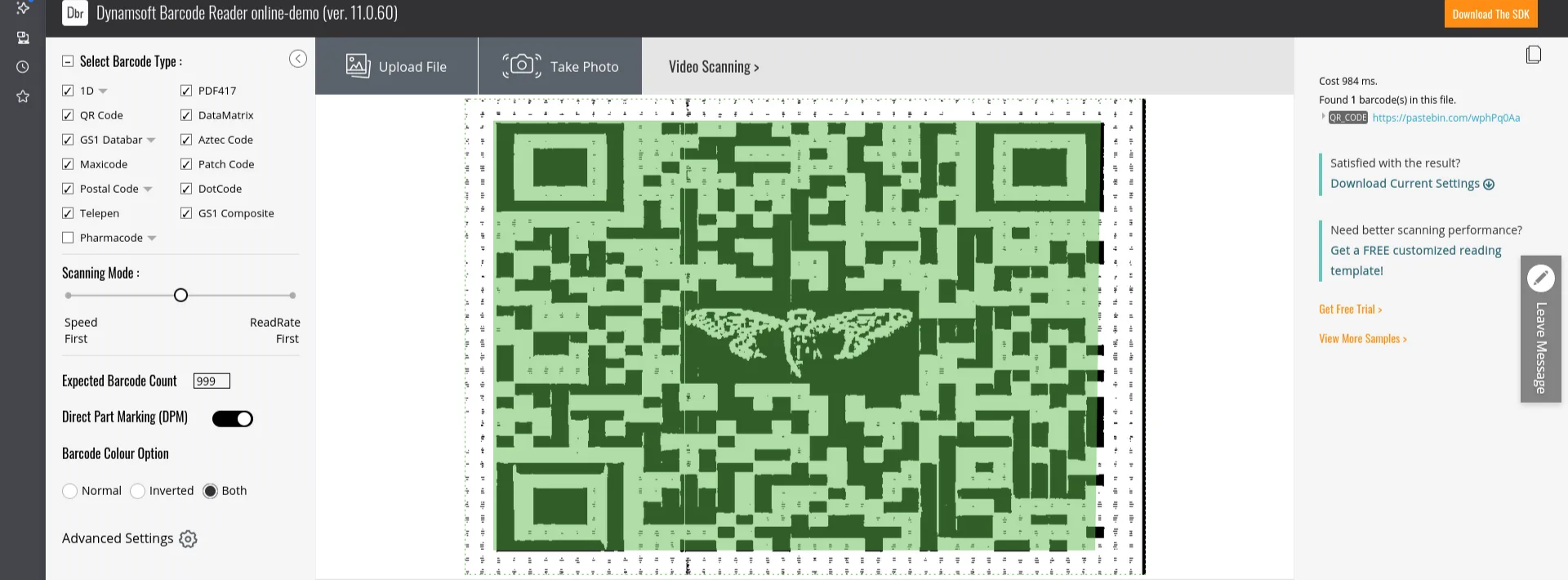
You can use this website to fix the barcode, then scan the barcode. It scanned a URL
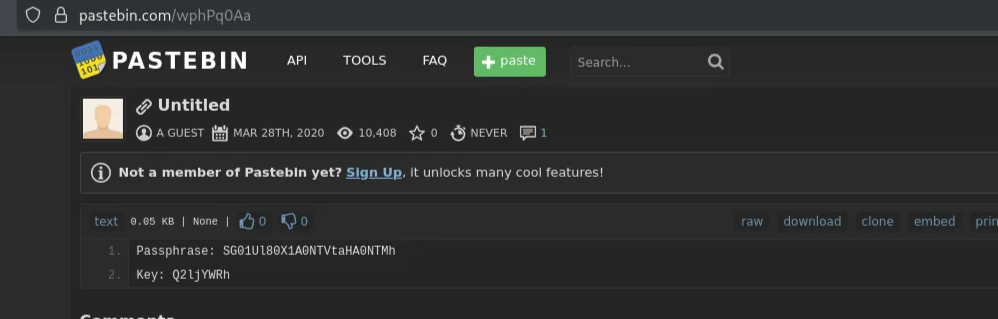
When followed the URL, this passphrase and key is related to the next task
Decode the passphrase
1
2
Passphrase: SG01Ul80X1A0NTVtaHA0NTMh
Key: Q2ljYWRh
Access the metadata of Welcome.jpg image
View the metadata of the image using exiftool
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
$ exiftool welcome.jpg
ExifTool Version Number : 12.57
File Name : welcome.jpg
Directory : .
File Size : 29 kB
File Modification Date/Time : 2020:04:15 01:59:40+03:00
File Access Date/Time : 2025:09:13 11:05:38+03:00
File Inode Change Date/Time : 2025:09:13 10:42:10+03:00
File Permissions : -rw-rw-r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Image Width : 509
Image Height : 503
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 509x503
Megapixels : 0.256
┌──(kali㉿kali)-[~/Documents/tryhackme/cicada]
└─$ xxd welcome.jpg | head
00000000: ffd8 ffe0 0010 4a46 4946 0001 0100 0001 ......JFIF......
00000010: 0001 0000 ffdb 0043 0008 0606 0706 0508 .......C........
00000020: 0707 0709 0908 0a0c 140d 0c0b 0b0c 1912 ................
00000030: 130f 141d 1a1f 1e1d 1a1c 1c20 242e 2720 ........... $.'
00000040: 222c 231c 1c28 3729 2c30 3134 3434 1f27 ",#..(7),01444.'
00000050: 393d 3832 3c2e 3334 32ff db00 4301 0909 9=82<.342...C...
00000060: 090c 0b0c 180d 0d18 3221 1c21 3232 3232 ........2!.!2222
00000070: 3232 3232 3232 3232 3232 3232 3232 3232 2222222222222222
00000080: 3232 3232 3232 3232 3232 3232 3232 3232 2222222222222222
00000090: 3232 3232 3232 3232 3232 3232 3232 ffc0 22222222222222..
I viewed the hexadecimal of the image just to make sure that the image format isn’t broken.
Decoding passphrase and the key with base64
1
2
3
4
5
$ echo "SG01Ul80X1A0NTVtaHA0NTMh" | base64 -d
Hm5R_4_P455mhp453!
$ echo "Q2ljYWRh" | base64 -d
Cicada
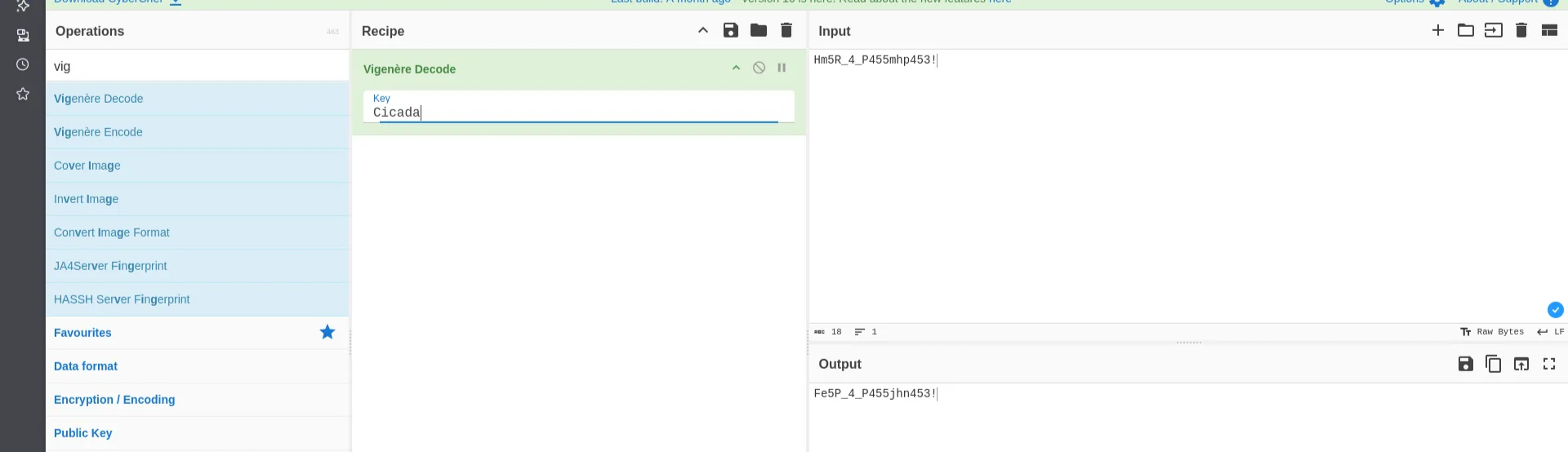
And this wasn’t the real passphrase, we need to decrypt it again with the Vigenère cipher as the hint described. According to wiki : The Vigenère cipher is a method of encrypting alphabetic text where each letter of the plaintext is encoded with a different Caesar cipher, whose increment is determined by the corresponding letter of another text, the key.
At first, it returned this:
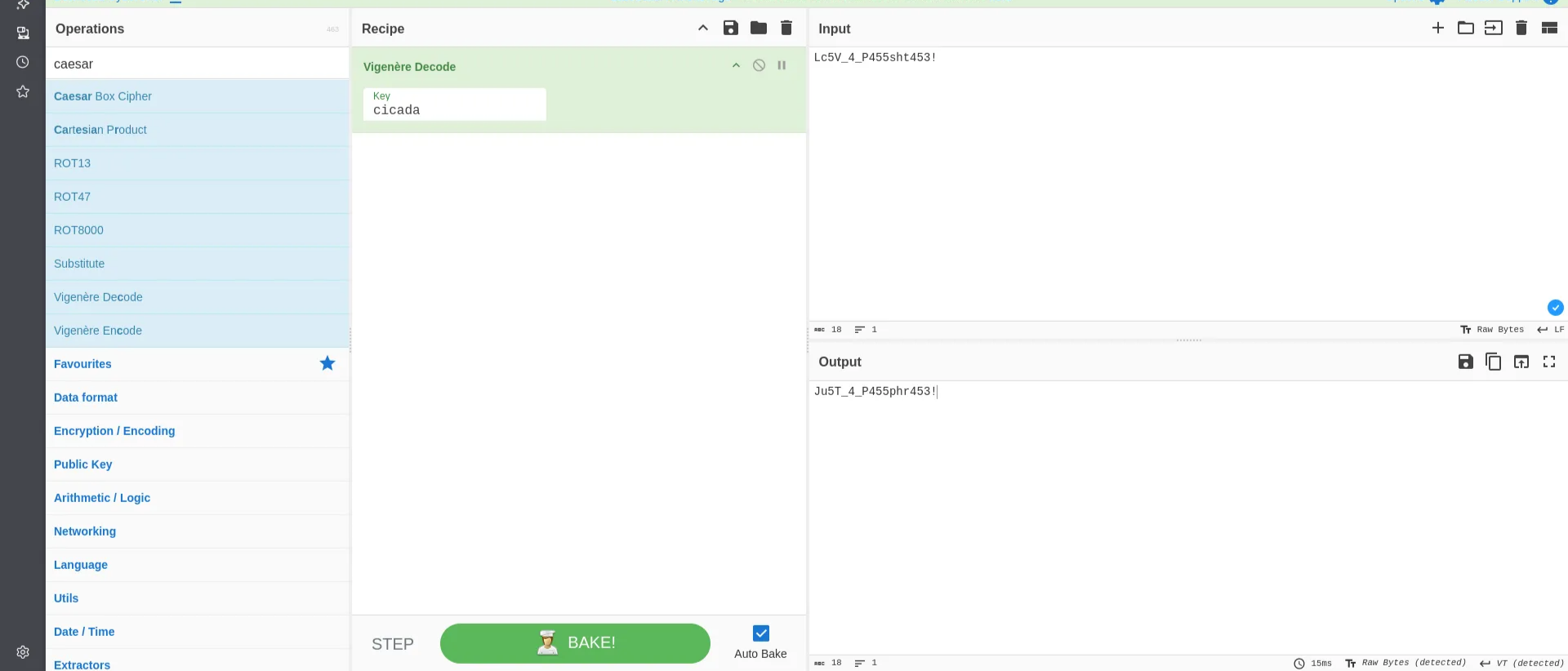
But that wasn’t the final password, so I decoded the returned result multiple times, till I got the right one.
1
Ju5T_4_P455phr453!
Gather Metadata
We can now extract the hidden text using this passphrase, this is done with steghide tool.
1
2
3
4
5
6
$ steghide extract -sf welcome.jpg -p Ju5T_4_P455phr453!
wrote extracted data to "invitation.txt".
┌──(kali㉿kali)-[~/Documents/tryhackme/cicada]
└─$ cat invitation.txt
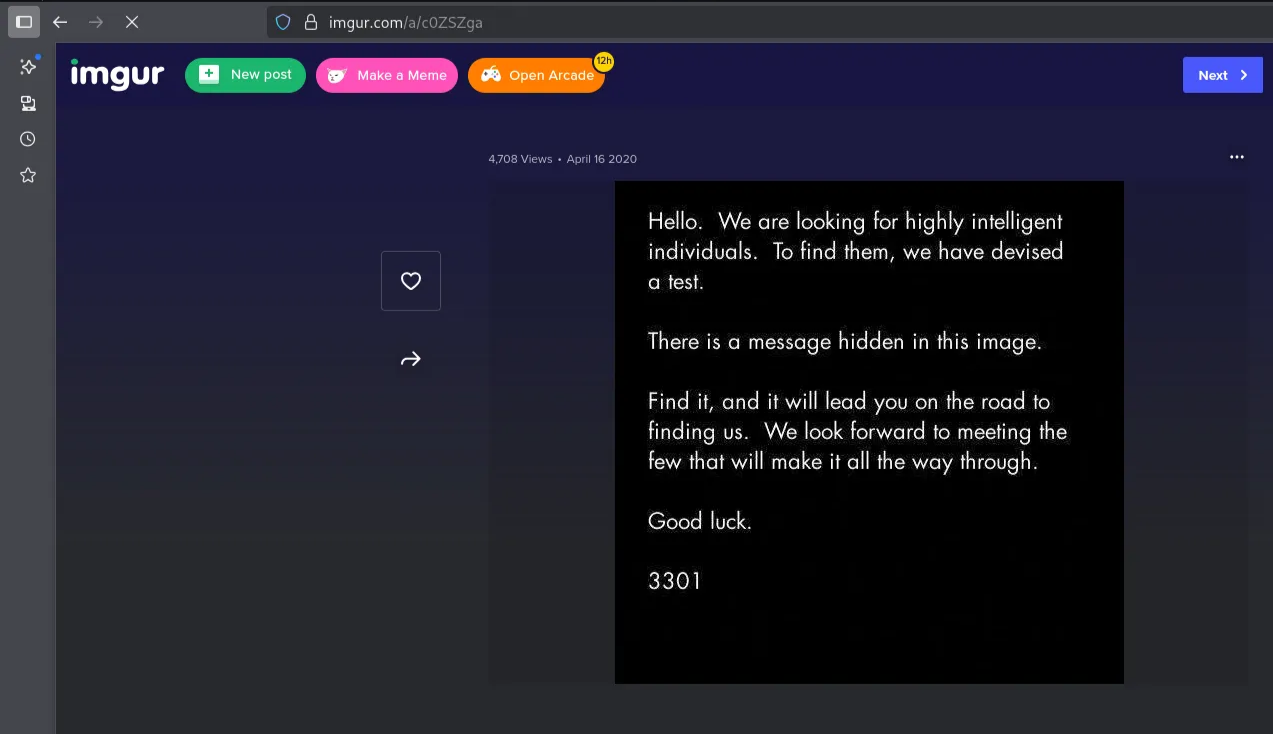
https://imgur.com/a/c0ZSZga
Following the URL
Save the image and jump to the next task.
Find Hidden Files
Here it is also asking to extract the hidden text inside the image we found from following URL of the previous task. This time we are going to use outguess to extract the hidden text
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
$ outguess -r 8S8OaQw.jpg extract
Reading 8S8OaQw.jpg....
Extracting usable bits: 29035 bits
Steg retrieve: seed: 38, len: 1351
┌──(kali㉿kali)-[~/Documents/tryhackme/cicada]
└─$ cat extract
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA1
Welcome again.
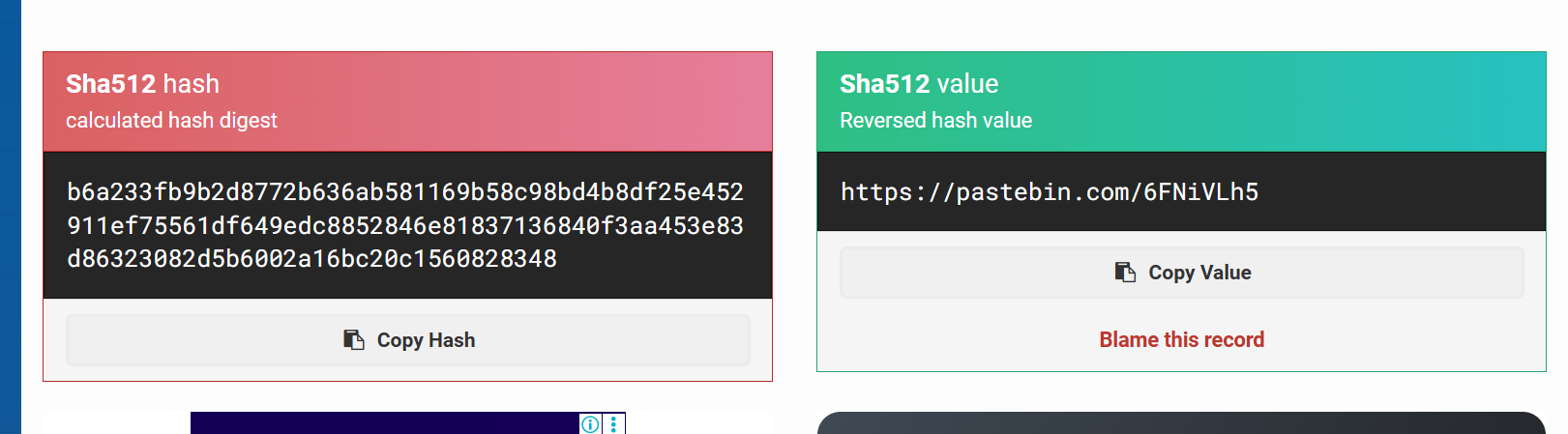
Here is a book code. To find the book, break this hash:
b6a233fb9b2d8772b636ab581169b58c98bd4b8df25e452911ef75561df649edc8852846e81837136840f3aa453e83d86323082d5b6002a16bc20c1560828348
Use positive integers to go forward in the text use negative integers to go backwards in the text.
I:1:6
I:2:15
I:3:26
I:5:4
I:6:15
I:10:26
/
/
I:13:5
I:13:1
I:14:7
I:3:29
I:19:8
I:22:25
/
I:23:-1
I:19:-1
I:2:21
I:5:9
I:24:-2
I:22:1
I:38:1
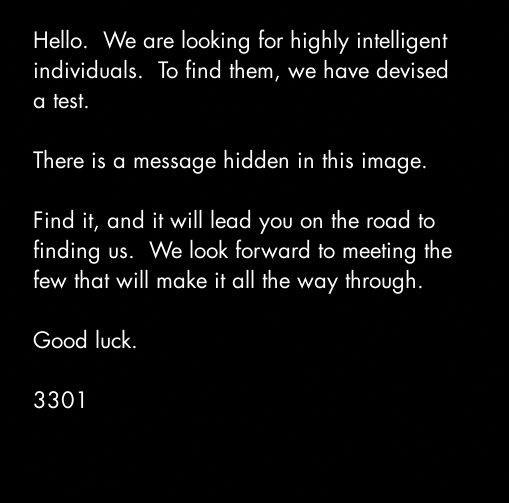
Good luck.
3301
-----BEGIN PGP SIGNATURE-----
Version: GnuPG v1.4.11 (GNU/Linux)
iQIcBAEBAgAGBQJQ5QoZAAoJEBgfAeV6NQkPf2IQAKWgwI5EC33Hzje+YfeaLf6m
sLKjpc2Go98BWGReikDLS4PpkjX962L4Q3TZyzGenjJSUAEcyoHVINbqvK1sMvE5
9lBPmsdBMDPreA8oAZ3cbwtI3QuOFi3tY2qI5sJ7GSfUgiuI6FVVYTU/iXhXbHtL
boY4Sql5y7GaZ65cmH0eA6/418d9KL3Qq3qkTcM/tRAHhOZFMZfT42nsbcvZ2sWi
YyrAT5C+gs53YhODxEY0T9M2fam5AgUIWrMQa3oTRHSoNAefrDuOE7YtPy40j7kk
5/5RztmAzeEdRd8QS1ktHMezXEhdDP/DEdIJCLT5eA27VnTY4+x1Ag9tsDFuitY4
2kEaVtCrf/36JAAwEcwOg2B/stdjXe10RHFStY0N9wQdReW3yAOBohvtOubicbYY
mSCS1Bx91z7uYOo2QwtRaxNs69beSSy+oWBef4uTir8Q6WmgJpmzgmeG7ttEHquj
69CLSOWOm6Yc6qixsZy7ZkYDrSVrPwpAZdEXip7OHST5QE/Rd1M8RWCOODba16Lu
URKvgl0/nZumrPQYbB1roxAaCMtlMoIOvwcyldO0iOQ/2iD4Y0L4sTL7ojq2UYwX
bCotrhYv1srzBIOh+8vuBhV9ROnf/gab4tJII063EmztkBJ+HLfst0qZFAPHQG22
41kaNgYIYeikTrweFqSK
=Ybd6
-----END PGP SIGNATURE----
Here just to show you when I tried to use steghide
1
2
3
$ steghide --extract -sf 8S8OaQw.jpg
Enter passphrase:
steghide: could not extract any data with that passphrase!
Why did outguess extracted the embedded data while steghide didn’t?
That’s because they differ on how to embed and extract the data. If you used outguess to embed a text, you can’t use steghide to extract it even if you have the right key, same thing applys to steghide.
- Steghide: According to this paper, the embedding algorithm works as follows:
- At first, the secret data is compressed and encrypted.
- Then uses your passphrase to seed a random number generator → picks random positions in the cover file to hide data.
- If a pixel/sample already has the right value, it skips changing it. Otherwise, it tries to pair up values so swapping them achieves the change (graph-theoretic matching).
- If swapping isn’t possible, it just overwrites some positions. Because most changes are swaps, the overall color/sample counts stay the same → making it hard to detect.
Note that in
steghidethe passphrase is mandatory, while inOutguessis optional- Outguess: According to this source;
- OutGuess uses a generic iterator object to select which bits in the data should be modified. A seed can be used to modify the behavior of the iterator. It is embedded in the data along with the rest of the message. By altering the seed, OutGuess tries to find a sequence of bits that minimizes the number of changes in the data that have to be made.
Book Cipher
Find the last clue, crack the hash, decipher the message
Copy the hash we found from the extracted data from “8S8OaQw.jpg”. Use hash-identifier to identify the hash type. Then use this source to crack the hash.
Another URL to follow.
1
https://pastebin.com/6FNiVLh5
We got a story, and we need to decipher it to get the message. Follow the instruction found on “8S8OaQw.jpg”.
Use positive integers to go forward in the text use negative integers to go backwards in the text.
The positive integers extracted from the story, for example:
- I:2:15 → This means, on line number 2, count forward 15 character (don’t count the spaces)
As for the negative integers, count from the instruction itself. for example:
- I:24:-2 → This means, count backward of this line two steps.
The final result:
1
https://bit.ly/39pw2NH
Follow the URL to get the name of the song. And Done!